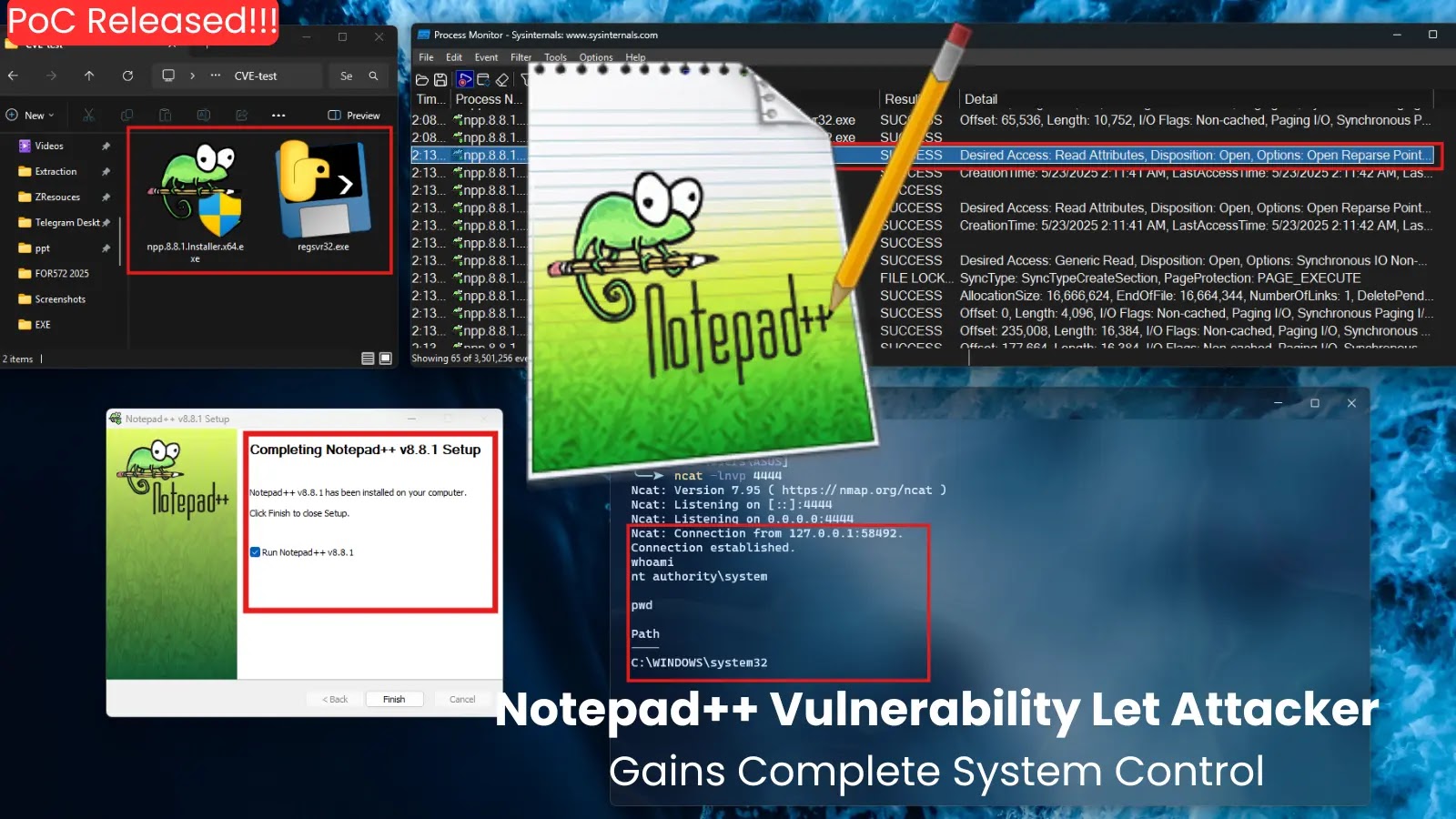
In late 2022, the cybersecurity community identified a new ransomware variant named CatB, also known as CatB99 or Baxtoy. This malware has garnered attention due to its sophisticated evasion techniques and unique attack methodologies. Notably, CatB employs DLL hijacking via the Microsoft Distributed Transaction Coordinator (MSDTC) service to deploy its malicious payloads, setting it apart from conventional ransomware strains.
Technical Analysis of CatB Ransomware
CatB’s attack sequence initiates with a dropper DLL that conducts environmental checks to detect virtualized environments, thereby evading analysis tools. This dropper then exploits the MSDTC service to load the primary ransomware payload through DLL hijacking. By manipulating the DLL search order, CatB ensures its malicious code is executed within a legitimate system process, effectively bypassing security defenses.
Once activated, CatB encrypts files on the compromised system. Unlike typical ransomware that appends new extensions to encrypted files, CatB maintains the original filenames, embedding ransom notes directly into the file headers. These notes demand Bitcoin payments, with amounts escalating from 50 BTC on the first day to 130 BTC by the fourth day, translating to approximately $800,000 to $2 million, depending on the timing of payment. The ransom note also offers victims the opportunity to decrypt up to three files for free as proof of decryption capability.
Evasion and Persistence Mechanisms
CatB incorporates several strategies to evade detection and maintain persistence:
– Virtual Environment Detection: The malware assesses system attributes such as RAM size, hard disk capacity, and CPU core count to identify virtual machines, thereby avoiding environments commonly used for malware analysis.
– DLL Hijacking via MSDTC: By exploiting the MSDTC service, CatB loads its payload into a trusted system process, complicating detection and removal efforts.
– Credential and Data Theft: Beyond encryption, CatB harvests sensitive information, including passwords, bookmarks, and browsing history from web browsers like Google Chrome, Microsoft Edge, and Mozilla Firefox, amplifying the potential damage to victims.
Potential Attribution and Evolution
Analyses suggest that CatB may be an evolution or rebranding of the Pandora ransomware, which was active earlier in 2022 and targeted sectors such as the automotive industry. Both ransomware families share code-level similarities and operational tactics. Furthermore, CatB has been linked to the ChamelGang (also known as CamoFei), a group associated with cyber-espionage activities. This connection indicates a possible shift in ransomware deployment strategies, blending financial extortion with intelligence gathering.
Mitigation and Defense Strategies
To defend against CatB and similar ransomware threats, organizations should implement the following measures:
1. Regular Software Updates: Ensure all systems and applications are up-to-date to mitigate vulnerabilities that ransomware can exploit.
2. Comprehensive Backups: Maintain regular backups of critical data in secure, offline locations to facilitate recovery without capitulating to ransom demands.
3. User Education: Conduct ongoing training programs to educate employees about phishing tactics and the importance of cautious behavior when handling emails and downloads.
4. Advanced Security Solutions: Deploy endpoint detection and response (EDR) systems capable of identifying and mitigating sophisticated threats like DLL hijacking.
5. Network Segmentation: Implement network segmentation to limit the spread of ransomware within an organization, containing potential damage.
Conclusion
CatB ransomware exemplifies the evolving complexity of cyber threats, utilizing advanced techniques such as DLL hijacking through the MSDTC service to evade detection and execute its payload. Its dual focus on data encryption and information theft underscores the necessity for organizations to adopt a multi-layered security approach. By staying informed about emerging threats and implementing robust defense mechanisms, organizations can enhance their resilience against sophisticated ransomware attacks like CatB.