The cybersecurity landscape in Latin America has been increasingly challenged by the activities of Blind Eagle, also known as APT-C-36. This threat actor has been active since at least 2018, persistently targeting entities across Colombia, Ecuador, Chile, Panama, and other nations in the region. Their operations have spanned various sectors, including government institutions, financial organizations, and the energy sector.
Adaptive Attack Strategies
Blind Eagle has demonstrated remarkable adaptability in its cyberattack strategies, seamlessly shifting between financially motivated attacks and espionage operations. This versatility is evident in their use of spear-phishing campaigns to distribute a range of publicly available Remote Access Trojans (RATs) such as AsyncRAT, BitRAT, Lime RAT, NjRAT, Quasar RAT, and Remcos RAT. By modifying these open-source tools, the group can tailor their campaigns to specific objectives, whether it’s cyber espionage or financial credential theft.
Sophisticated Phishing Techniques
The group’s attack chains often commence with phishing emails that impersonate legitimate governmental institutions and financial entities. These emails typically contain urgent messages prompting recipients to click on malicious links or open attachments, leading to malware infection. To enhance the effectiveness of these campaigns, Blind Eagle employs geolocation filtering via URL shorteners, ensuring that only users from targeted countries are redirected to malicious sites, while others are sent to legitimate websites. This tactic not only increases the success rate of their attacks but also complicates detection and analysis efforts.
Multi-Stage Infection Process
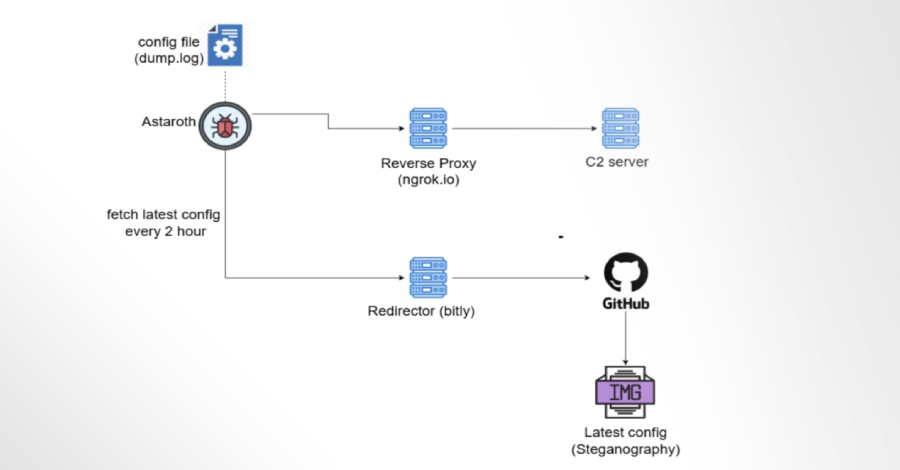
Once a victim interacts with the malicious link or attachment, a multi-stage infection process is initiated. The initial dropper, often a compressed ZIP archive, contains a Visual Basic Script (VBS) responsible for retrieving the next-stage payload from a hard-coded remote server. These servers can range from image hosting sites and Pastebin to legitimate services like Discord and GitHub. The second-stage malware, frequently obfuscated using steganographic methods, is a DLL or .NET injector that subsequently contacts another malicious server to retrieve the final stage trojan.
Evasion Techniques
To evade detection, Blind Eagle employs sophisticated techniques such as process injection, particularly process hollowing. This method involves creating a legitimate process in a suspended state, unmapping its memory, replacing it with a malicious payload, and then resuming the process to start execution. By executing the RAT within the memory of a legitimate process, the group effectively bypasses process-based defenses, making it challenging for security solutions to detect and mitigate the threat.
Exploitation of Vulnerabilities
In addition to their phishing and evasion tactics, Blind Eagle has been observed exploiting known vulnerabilities to enhance their attack efficacy. Notably, they have utilized a variant of an exploit for a now-patched Microsoft Windows flaw (CVE-2024-43451), which allows attackers to extract NTLMv2 hashes for authentication attacks. The group demonstrated remarkable adaptability by weaponizing this vulnerability just six days after the release of a Microsoft patch, integrating this attack vector into their operations.
Use of Legitimate Platforms for Malware Distribution
Blind Eagle has also been known to deliver malware through legitimate file-sharing platforms, including Google Drive, Dropbox, Bitbucket, and GitHub. This approach complicates detection by security systems, as the use of trusted platforms can bypass traditional security measures. An operational oversight revealed a deleted file from a GitHub repository containing sensitive information, including usernames, passwords, and ATM PINs of individuals and organizations in Colombia. This incident underscores the group’s ability to exploit legitimate platforms to evade security measures and distribute malware effectively.
Implications and Recommendations
The activities of Blind Eagle highlight the evolving nature of cyber threats in Latin America. Their ability to adapt tactics, exploit vulnerabilities, and leverage legitimate platforms for malicious purposes poses significant challenges for cybersecurity defenses. Organizations, particularly those in targeted sectors, must remain vigilant and implement comprehensive security measures, including employee training on phishing awareness, regular system updates to patch vulnerabilities, and the deployment of advanced threat detection solutions capable of identifying sophisticated evasion techniques.