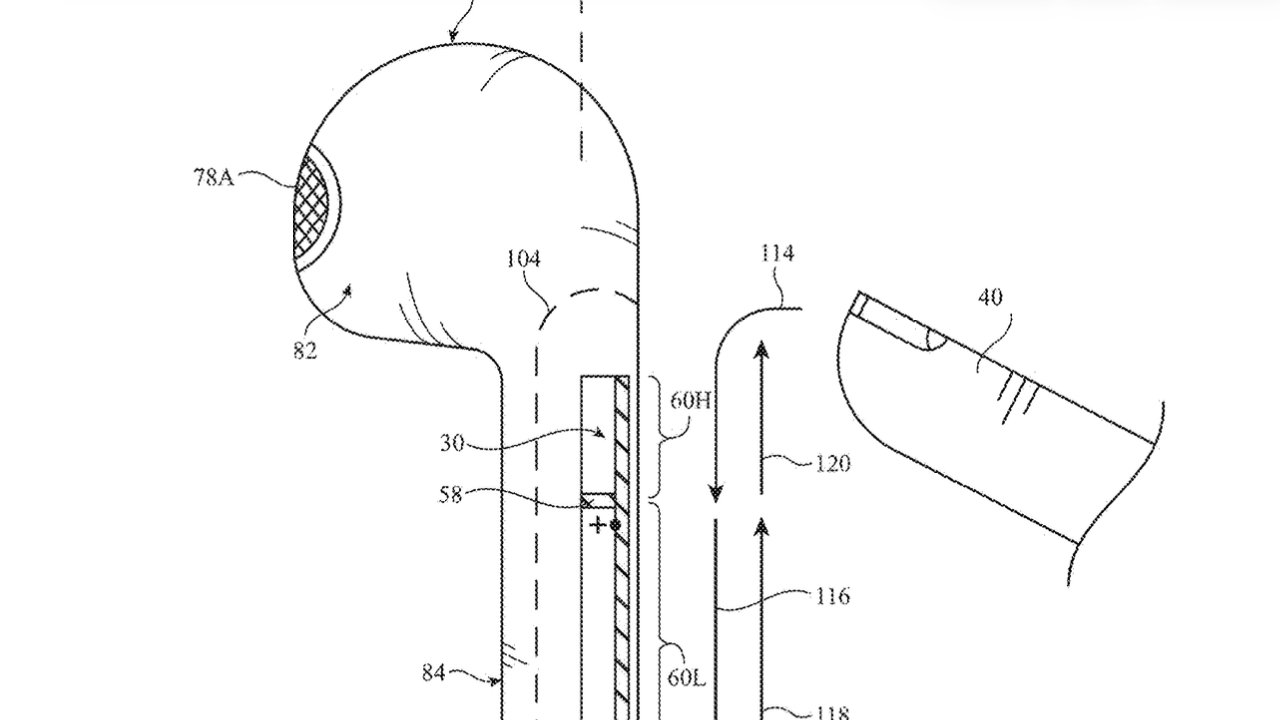
Apple’s Next-Gen AirPods: Revolutionizing Gesture Control with Advanced Antenna Technology Apple is poised to redefine user interaction with its AirPods by integrating advanced gesture recognition […]
Author: The Daily Tech Feed Team
Apple Set to Announce Potential Record Q1 2026 Earnings on January 29, Driven by iPhone 17 and Service Revenues
Apple’s Anticipated Record-Breaking Q1 2026 Earnings Report Set for January 29 Apple Inc. is poised to announce its fiscal first-quarter earnings for 2026 on Thursday, […]
Bluetti Showcases Innovative Power Solutions for Home, Travel, and Sustainability at CES 2026
Bluetti Unveils Cutting-Edge Power Solutions at CES 2026 for Home, Vehicle, and Outdoor Use At CES 2026, Bluetti introduced a suite of innovative power solutions […]
Apple Sets 2026 Shareholder Meeting for Feb 24; Key Issues Include China Operations, Exec Pay
Apple’s 2026 Annual Shareholder Meeting Set for February 24 Apple Inc. has scheduled its annual shareholder meeting for February 24, 2026, at 11 a.m. Eastern […]
Apple TV+ Earns 12 Nominations at 32nd Actor Awards, Led by Hit Comedy ‘The Studio
Apple TV+ Dominates 32nd Actor Awards with 12 Nominations, Led by ‘The Studio’ Apple TV+ continues to make significant strides in the entertainment industry, securing […]
Apple Wins Ninth Circuit Ruling in Antitrust Case Against AliveCor Over Watch Technology
Apple Triumphs in Latest Legal Battle Against AliveCor Over Apple Watch Sensor In a significant legal victory for Apple, the Court of Appeals for the […]
Amazon January Sale Slashes AirPods Pro 3 Price to $199.99, Matches Lowest Ever for Premium Earbuds
Amazon’s January Sale: AirPods Pro 3 Now Available at $199.99 In an exciting development for tech enthusiasts, Amazon has reduced the price of Apple’s AirPods […]
iOS 26 Adoption Sluggish: Only 16% of iPhone Users on Latest Version Despite New Features and Security Risks
iOS 26 Adoption Lags Behind Previous Versions: Analyzing the Slow Uptake Four months after its release in September 2025, iOS 26 has been adopted by […]
Apple Details 2025 Executive Pay: Tim Cook Earns $74.3M, Other Leaders’ Salaries Released
Apple’s 2025 Executive Compensation: A Detailed Breakdown Apple Inc. has released its annual proxy statement, providing a comprehensive overview of executive compensation for the fiscal […]
Elizabeth Olsen’s Eternity Premieres on Apple TV for Valentine’s Release
Elizabeth Olsen’s ‘Eternity’ Premieres on Apple TV This Valentine’s Day Apple TV has officially announced the streaming release date for its latest romantic comedy, Eternity, […]