In the ever-evolving landscape of cybersecurity, staying ahead of emerging threats is paramount for Security Operations Centers (SOC) and Digital Forensics and Incident Response (DFIR) teams. ANY.RUN’s Threat Intelligence (TI) Feeds have emerged as a pivotal resource, offering a continuous stream of unique and up-to-date Indicators of Compromise (IOCs). By harnessing data from a global community of over 500,000 researchers and security professionals, ANY.RUN provides actionable intelligence that enhances threat detection and mitigation strategies.
Sourcing Threat Intelligence: A Community-Driven Approach
ANY.RUN’s TI Feeds are built upon a robust foundation of community-sourced data. Cybersecurity professionals worldwide contribute by uploading and analyzing real-world malware and phishing samples. This collaborative effort ensures a steady influx of contemporary threat samples, reflecting the latest malicious activities and emerging threat patterns. Unlike traditional models that may rely heavily on historical data, this dynamic approach offers a real-time snapshot of the threat landscape, enabling organizations to respond proactively.
Comprehensive IOC Coverage with Contextual Enrichment
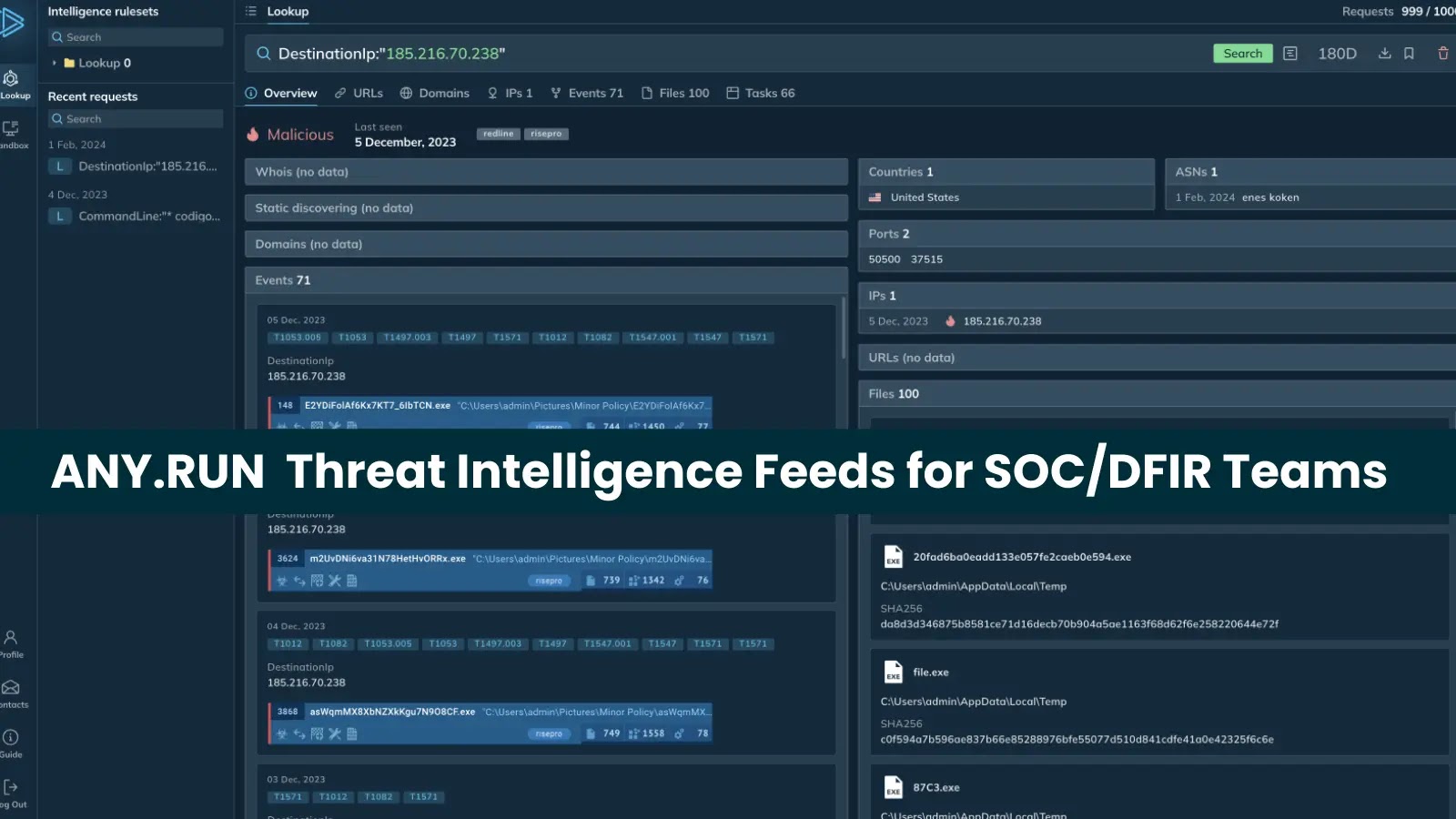
The TI Feeds from ANY.RUN encompass a wide array of indicators, each assigned a reliability score ranging from 50 (suspicious) to 100 (highly reliable). These indicators include:
– IP Addresses: Identifying addresses associated with command-and-control (C2) servers or phishing campaigns.
– Malicious Domains: Highlighting domains that serve as hubs for multiple IPs or malware instances within coordinated campaigns.
– URLs: Detecting gateways used for malware distribution or phishing operations.
Each indicator is enriched with contextual information such as threat scores, threat names, types, detection timestamps, and related file hashes. This depth of context empowers security teams to prioritize alerts effectively and respond with precision.
Unique Methods for IOC Extraction: Setting ANY.RUN Apart
ANY.RUN distinguishes itself through innovative methodologies for extracting IOCs, yielding indicators that may not be accessible via other intelligence services. Two primary techniques underscore this uniqueness:
1. Malware Configuration Extraction:
ANY.RUN’s Interactive Sandbox automatically parses configurations from malware samples, extracting hardcoded IOCs such as C2 server addresses, encryption keys, and attack parameters. This process provides direct insight into the operational infrastructure of active threats. For instance, analyzing an AsyncRAT sample reveals the extracted configuration, including the malicious IP address used for C2 communications, which is then integrated into the TI Feeds system.
2. Network Traffic Analysis via Suricata IDS:
By leveraging Suricata Intrusion Detection System (IDS) rules, ANY.RUN identifies patterns in network traffic indicative of malicious activity. This behavioral analysis detects threats even when attackers modify their infrastructure, focusing on the tactics and techniques employed rather than static indicators. For example, detecting FormBook’s C2 traffic through Suricata rules allows for the identification and mitigation of this malware’s activities.
Core Advantages for SOC and DFIR Teams
ANY.RUN’s TI Feeds offer several key benefits that enhance the operational efficiency of SOC and DFIR teams:
– Fresh, Processed Threat Intelligence:
IOCs are updated every few hours, ensuring access to the latest threat data. Advanced algorithms and proprietary technology filter and validate this data, reducing noise and false positives.
– Rich Contextual Enrichment:
Each IOC is linked to corresponding sandbox sessions, providing access to memory dumps, network traffic, behavior patterns, and more. This context aids in understanding the broader implications of threats.
– Seamless Integration with Security Platforms:
Delivered in standardized formats such as STIX and MISP, the TI Feeds integrate effortlessly with existing SIEMs and TIPs, including platforms like Splunk, OpenCTI, and ThreatConnect.
– Improved Operational Efficiency:
Access to fresh IOCs streamlines threat hunting activities, enabling teams to focus on emerging threats with precision. This capability reduces Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), enhancing overall incident response effectiveness.
Integration and Compatibility: Enhancing Security Infrastructure
ANY.RUN’s TI Feeds are designed for easy integration into existing security infrastructures. By providing data in standardized formats, organizations can seamlessly incorporate these feeds into their SIEM and TIP systems. This integration extends threat coverage, improves incident response processes, and strengthens the overall security posture. Furthermore, the feeds support API integration, allowing for real-time threat updates and automated responses, thereby optimizing threat hunting activities and operational efficiency.
Conclusion: Empowering Proactive Cyber Defense
In the face of rapidly evolving cyber threats, ANY.RUN’s enhanced Threat Intelligence Feeds provide SOC and DFIR teams with the tools necessary to detect, analyze, and respond to threats effectively. By leveraging a global community of cybersecurity professionals and employing unique methods for IOC extraction, ANY.RUN delivers fresh, actionable intelligence that enhances threat detection capabilities. The seamless integration with existing security platforms and the provision of rich contextual data further empower organizations to maintain a proactive defense against emerging cyber threats.