In a recent cybersecurity development, the threat actor known as EncryptHub has been identified exploiting a previously unknown vulnerability in Microsoft Windows to deploy a variety of malicious software, including the Rhadamanthys and StealC information stealers. This zero-day vulnerability, designated as CVE-2025-26633 with a CVSS score of 7.0, pertains to an improper neutralization issue within the Microsoft Management Console (MMC). Microsoft addressed this flaw in their March 2025 Patch Tuesday update.
Understanding CVE-2025-26633
CVE-2025-26633 is a security vulnerability that allows attackers to bypass certain security features locally by manipulating the MMC framework. The MMC is a core component of Windows that provides a unified interface for system management. By exploiting this vulnerability, attackers can execute arbitrary code on the affected system without the user’s knowledge.
The Attack Mechanism
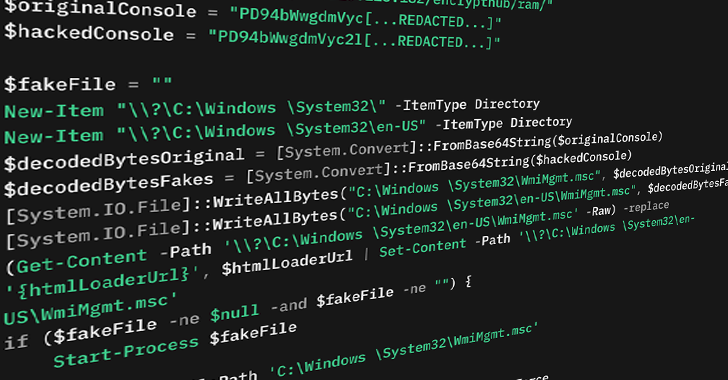
Trend Micro researchers have detailed the methods employed by EncryptHub to exploit this vulnerability. The attack involves the creation of two Microsoft Console (.msc) files with identical names: one legitimate and one malicious. These files are placed in specific directories to manipulate the MMC’s Multilingual User Interface Path (MUIPath) feature. When the legitimate .msc file is executed, the MMC inadvertently loads and runs the malicious counterpart due to the MUIPath manipulation.
This technique, referred to as “MSC EvilTwin,” leverages the MMC’s behavior of prioritizing certain directories when loading files. By placing the malicious .msc file in a directory named “en-US,” the attacker ensures that the MMC loads this file instead of the legitimate one. This method effectively bypasses standard security measures and allows the execution of malicious code.
Additional Exploitation Methods
EncryptHub has also been observed utilizing other methods to execute malicious payloads using .msc files:
1. ExecuteShellCommand Method: This approach involves using the ExecuteShellCommand method of the MMC to download and execute additional payloads on the victim’s machine. This technique was previously documented by cybersecurity firm Outflank in August 2024.
2. Mock Trusted Directories: By creating directories that mimic trusted system paths, such as “C:\Windows \System32” (note the space after “Windows”), attackers can bypass User Account Control (UAC) prompts. In this scenario, a malicious .msc file named “WmiMgmt.msc” is placed in the mock directory, leading to its execution without triggering security alerts.
Delivery Methods and Payloads
The initial infection vector in these attacks often involves victims downloading digitally signed Microsoft Installer (MSI) files that impersonate legitimate Chinese software applications like DingTalk or QQTalk. Once executed, these MSI files retrieve and run the MSC EvilTwin loader from a remote server. This loader then facilitates the deployment of various malicious payloads, including:
– Rhadamanthys Infostealer: A malware designed to steal sensitive information from infected systems.
– StealC Infostealer: Another information-stealing malware that targets credentials and other personal data.
– DarkWisp and SilentPrism Backdoors: Malicious programs that provide unauthorized remote access to compromised systems.
Trend Micro’s analysis indicates that EncryptHub has been experimenting with these techniques since April 2024. The campaign is under active development, employing multiple delivery methods and custom payloads designed to maintain persistence and exfiltrate sensitive data to the attackers’ command-and-control servers.
Implications and Recommendations
The exploitation of CVE-2025-26633 by EncryptHub underscores the critical importance of timely software updates and vigilant cybersecurity practices. Organizations and individuals are strongly advised to:
– Apply Security Patches Promptly: Ensure that all systems are updated with the latest security patches provided by Microsoft to mitigate known vulnerabilities.
– Exercise Caution with Downloads: Be wary of downloading and executing files from untrusted sources, especially those that mimic legitimate software applications.
– Implement Robust Security Measures: Utilize comprehensive security solutions that can detect and prevent the execution of malicious code.
– Monitor System Activity: Regularly review system logs and network traffic for signs of unusual activity that may indicate a compromise.
By adopting these practices, users can reduce the risk of falling victim to sophisticated attacks like those orchestrated by EncryptHub.