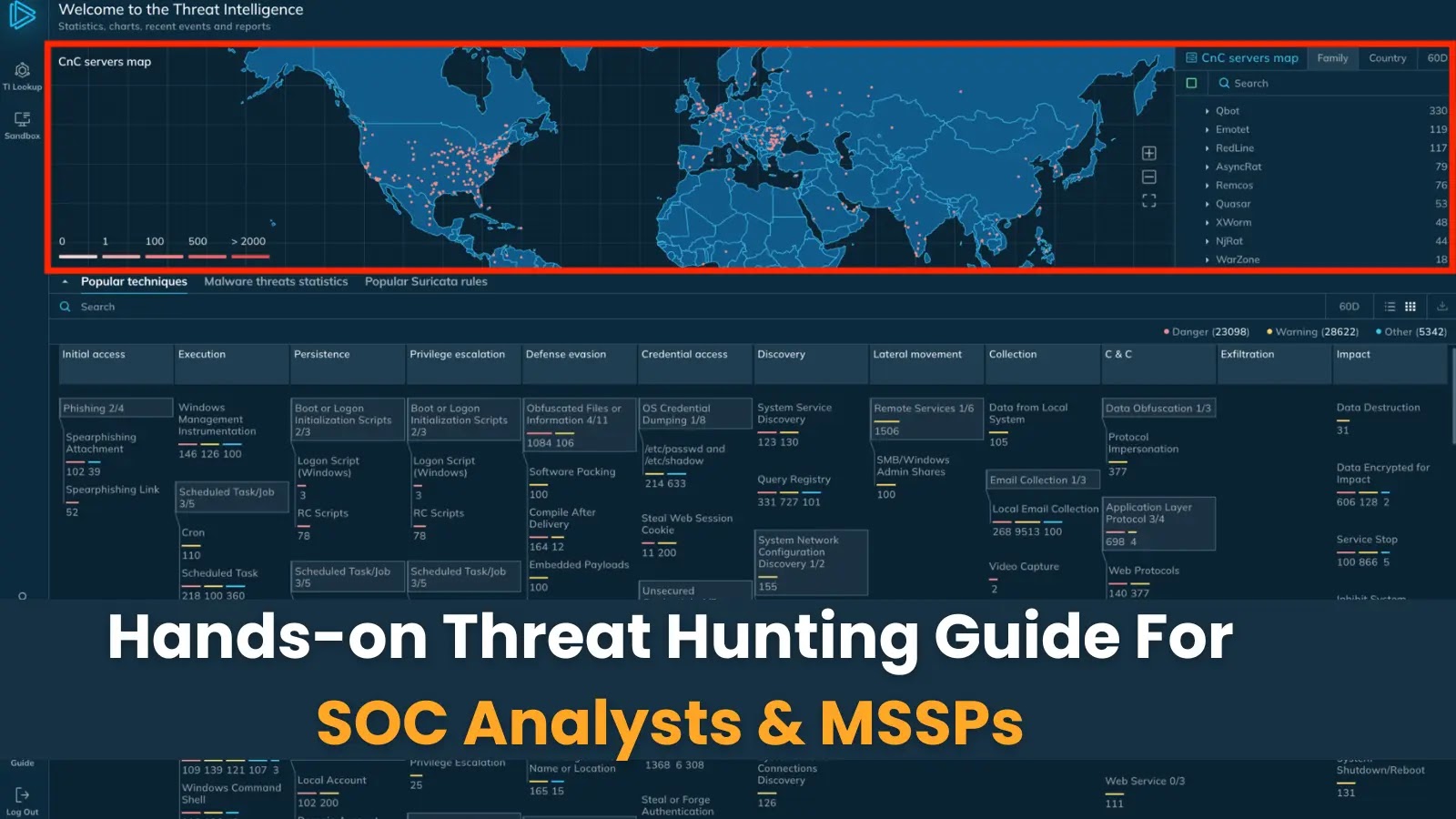
In the ever-evolving landscape of cyber threats, Security Operations Center (SOC) analysts and Managed Security Service Providers (MSSPs) must adopt proactive threat-hunting strategies to stay ahead of adversaries. Traditional detection methods often fall short against sophisticated attack techniques. This guide offers practical approaches to enhance threat-hunting capabilities, focusing on advanced query techniques, behavioral analysis, and integration with frameworks like MITRE ATT&CK.
Advanced Query Techniques for Effective Threat Hunting
A cornerstone of effective threat hunting is the ability to construct precise queries that sift through vast datasets to identify potential threats. Utilizing advanced query syntax with over 40 parameters allows analysts to perform highly specific and contextualized searches. The basic structure of these queries typically includes a parameter, a colon, and a value, often enclosed in quotation marks. Logical operators such as AND, OR, and NOT are essential:
– AND: Requires both conditions to be true.
– OR: Requires at least one condition to be true.
– NOT: Excludes results that match specific conditions.
Incorporating wildcards and special characters enhances query flexibility:
– Asterisk (): Represents any number of characters.
– Question mark (?): Represents a single character.
– Caret (^): Matches the beginning of a string.
– Dollar sign ($): Matches the end of a string.
These elements enable analysts to create precise searches across file properties, process activities, network communications, registry operations, and threat classifications.
Leveraging Threat Intelligence Platforms
Threat Intelligence Platforms (TIPs) are invaluable in aggregating and analyzing data from various sources, providing a comprehensive view of potential threats. For instance, platforms like ANY.RUN offer access to extensive malware databases, continuously updated by a global community of users, including numerous corporate SOC teams. These platforms support sophisticated query syntax, enabling highly specific and contextualized searches that can yield relevant analysis sessions, malware samples, or indicators for further research.
Key Functions of Threat Intelligence Platforms:
1. IOC Lookups: Facilitate detailed investigations of traditional indicators of compromise, including IP addresses, cryptographic hashes (MD5, SHA-1, SHA-256), domain names, and URLs, providing foundational threat identification capabilities.
2. Behavioral Lookups: Extend beyond static indicators by analyzing system activities such as registry modifications, process executions, network communications, and mutex creations. This approach is particularly effective for detecting novel threats lacking established signatures or fileless attacks leveraging living-off-the-land techniques.
3. MITRE Techniques Detection: Integrates the ATT&CK framework, enabling structured hunting for specific adversary tactics, techniques, and procedures (TTPs) through parameterized searches that map to documented attack sequences.
4. File/Event Correlation: Identifies relationships between disparate attack components, revealing comprehensive threat chains by linking artifacts like mutex creations, registry modifications, and network communications.
5. YARA-Based Threat Hunting: Utilizes YARA rules to detect and classify malware families based on textual or binary patterns, allowing analysts to create custom rules tailored to their organization’s threat landscape.
6. Interactive Analysis Sessions: Provides dynamic analysis environments where analysts can observe malware behavior in real-time, facilitating a deeper understanding of threat mechanisms and aiding in the development of effective detection and mitigation strategies.
Integrating Behavioral Analysis and MITRE ATT&CK Framework
Behavioral analysis focuses on understanding the actions and patterns of malware within a system. By observing behaviors such as process executions, file system changes, registry modifications, and network activity, analysts can identify anomalies indicative of malicious activity. This approach is crucial for detecting threats that evade traditional signature-based detection methods.
The MITRE ATT&CK framework offers a comprehensive knowledge base of adversary tactics and techniques based on real-world observations. Integrating this framework into threat-hunting activities allows analysts to:
– Map Observed Behaviors to Known Tactics: By aligning detected activities with specific ATT&CK techniques, analysts can understand the context and objectives of an attack.
– Develop Hypothesis-Driven Hunts: Using the framework to inform hypotheses about potential threats, guiding focused hunting activities.
– Enhance Detection Capabilities: By identifying gaps in existing detection mechanisms and developing new detection rules based on ATT&CK techniques.
Best Practices for Effective Threat Hunting
To maximize the effectiveness of threat-hunting efforts, SOC analysts and MSSPs should adopt the following best practices:
1. Continuous Training and Skill Development: Cyber threats evolve rapidly; therefore, ongoing education and training are essential. Analysts should stay updated on emerging threats, attack techniques, and vulnerabilities through industry conferences, webinars, and certifications.
2. Establish Baselines for Normal Activity: Understanding what constitutes normal behavior within an organization’s systems and networks allows analysts to detect anomalies more effectively.
3. Collaborate and Share Information: Threat hunting is a team effort. Collaboration with other teams, such as incident response and threat intelligence, enhances the effectiveness of hunting activities.
4. Leverage Automation: Automating routine tasks like data collection, log analysis, and initial triage allows analysts to focus on more complex investigations.
5. Document and Review Hunting Activities: Maintaining detailed records of hunting activities, findings, and lessons learned supports continuous improvement and knowledge sharing within the team.
Challenges in Threat Hunting and Solutions
Despite its benefits, threat hunting presents several challenges:
– Resource Constraints: Limited analyst time and competing priorities can hinder hunting efforts. Solutions include starting with focused hunting activities, leveraging automation, and considering managed hunting services for supplemental expertise.
– Data Limitations: Insufficient data collection or retention can impede effective hunting. Organizations should identify critical data gaps, prioritize collection, and implement staged data expansion focused on high-value sources.
– Skill Development: A shortage of analysts with hunting expertise can be addressed by developing internal training programs, creating mentorship opportunities, and utilizing external training resources.
– Alert Fatigue: The volume of alerts can overwhelm analysts. Implementing protected hunting time, using automation to reduce alert processing burden, and focusing hunting on gaps in automated detection can mitigate this issue.
Conclusion
Proactive threat hunting is essential for SOC analysts and MSSPs to detect and mitigate sophisticated cyber threats. By mastering advanced query techniques, leveraging threat intelligence platforms, integrating behavioral analysis, and aligning with frameworks like MITRE ATT&CK, security teams can enhance their detection capabilities and reduce response times. Continuous training, collaboration, and the strategic use of automation further bolster the effectiveness of threat-hunting efforts, ensuring organizations remain resilient against evolving cyber threats.