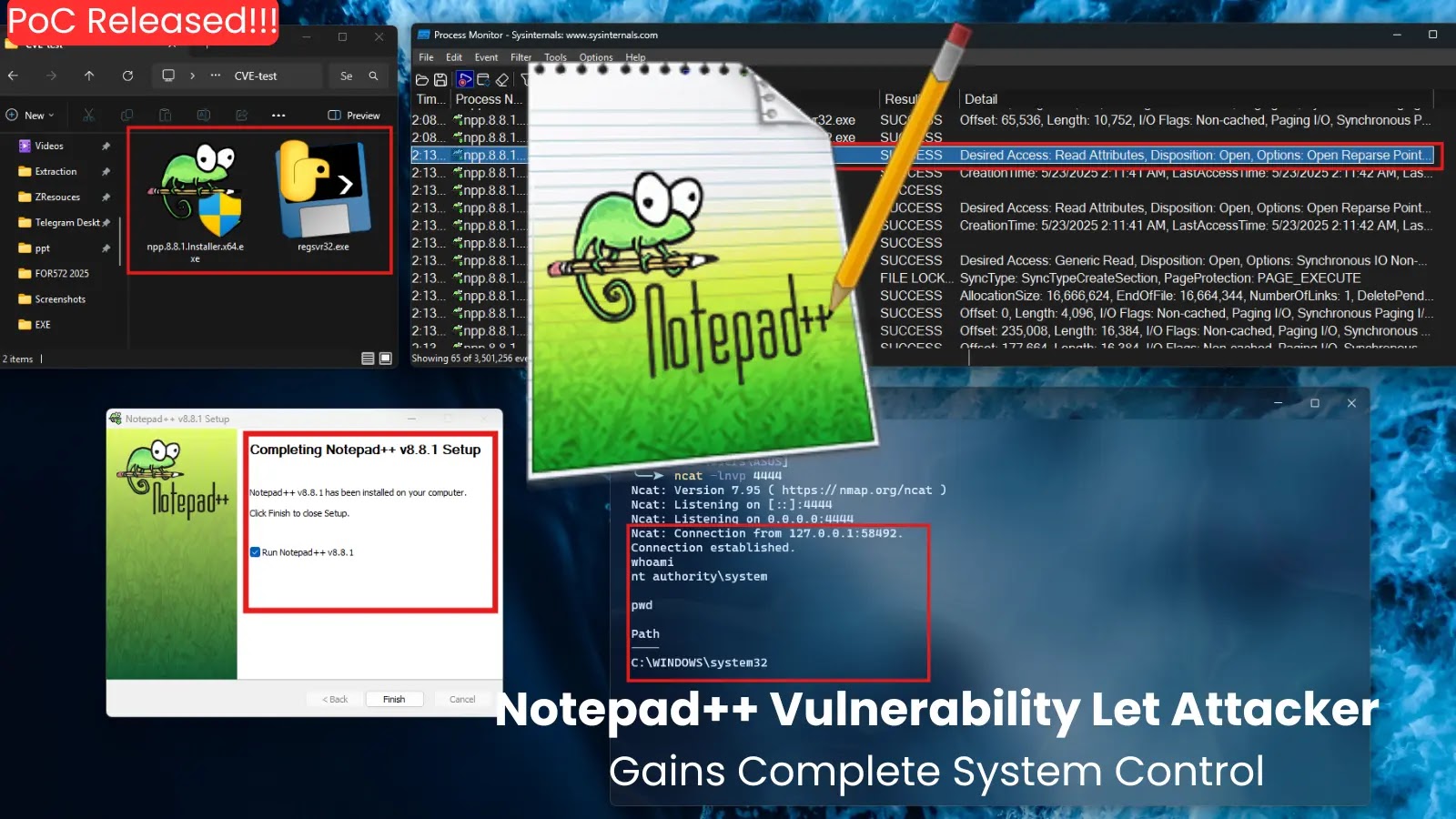
A critical security vulnerability has been identified in Notepad++ version 8.8.1, potentially allowing attackers to gain complete control over affected systems. This flaw, designated as CVE-2025-49144, exploits a binary planting technique that can escalate privileges to the SYSTEM level. A proof-of-concept (PoC) demonstrating this exploit has been publicly released, raising significant concerns about the security of systems running this version of Notepad++.
Vulnerability Details
The vulnerability resides in the Notepad++ v8.8.1 installer, released on May 5, 2025. It stems from an uncontrolled executable search path, which can be exploited for local privilege escalation attacks. Specifically, the installer searches for executable dependencies in the current working directory without proper verification. This oversight allows malicious actors to inject harmful code into the installation process.
The risk is particularly high due to the minimal user interaction required for exploitation. By leveraging the standard Windows DLL search order mechanism, attackers can place malicious executables that are automatically loaded with elevated privileges during the installation process.
Exploitation Methodology and Proof of Concept
Exploiting this vulnerability is alarmingly straightforward. An attacker can place a malicious executable, such as a compromised version of `regsvr32.exe`, in the same directory as the Notepad++ installer. When the installer is executed, the system automatically loads the malicious file with SYSTEM privileges, granting the attacker full control over the target machine.
Process Monitor logs included in the PoC materials demonstrate the installer’s vulnerability by showing its search for executables in the current directory. The publicly released demonstration includes video evidence confirming successful exploitation, highlighting the ease with which this vulnerability can be abused.
Potential Impact
Notepad++ boasts a substantial global user base, with the software’s official website receiving over 1.6 million monthly visits as of June 2025. The text editor holds approximately 1.33% market share in the Integrated Development Environments (IDEs) and text editors category, translating to hundreds of thousands of potentially vulnerable installations worldwide.
The vulnerability poses particularly severe risks given Notepad++’s popularity among developers, IT professionals, and general users across various industries. In corporate environments, successful exploitation could lead to data breaches, lateral movement within networks, and complete system compromise.
Context and Precedents
This incident is part of a growing pattern of installer vulnerabilities affecting popular software applications. Previous Notepad++ versions have faced similar security challenges, including CVE-2023-6401 and CVE-2023-47452, which also involved DLL hijacking and privilege escalation vulnerabilities.
The vulnerability aligns with current cybersecurity threat trends, where attackers increasingly target trusted software distribution mechanisms. According to the 2025 Global Cybersecurity Outlook, supply chain attacks and software installer vulnerabilities represent critical emerging threats in the current security landscape.
Mitigation and Response
In response to this critical vulnerability, Notepad++ developers have swiftly released version 8.8.2 to address the issue. The patch implements secure library loading practices and absolute path verification for executable dependencies, following Microsoft’s secure loading guidance.
Users are strongly advised to update to the latest version immediately to mitigate the risk. To update Notepad++, users can visit the official website and download the latest installer. It is also recommended to verify the integrity of the downloaded files by checking their digital signatures.
Recommendations for Users
To protect systems from potential exploitation, users should take the following steps:
1. Update Notepad++: Ensure that you are running version 8.8.2 or later.
2. Verify Installer Integrity: Before executing the installer, check its digital signature to confirm its authenticity.
3. Monitor System Activity: Regularly review system logs for unusual activities, especially during software installations.
4. Limit Administrative Privileges: Operate with the least privilege necessary to reduce the impact of potential exploits.
5. Educate Users: Inform all users about the importance of downloading software from official sources and verifying file integrity.
Conclusion
The discovery of CVE-2025-49144 in Notepad++ version 8.8.1 underscores the critical importance of secure software development and distribution practices. Users must remain vigilant, promptly apply security updates, and adhere to best practices to safeguard their systems against such vulnerabilities.