A significant security flaw has been identified in Windows Server 2025, potentially allowing attackers to escalate privileges and compromise any user within Active Directory (AD). This vulnerability exploits the Delegated Managed Service Account (dMSA) feature, a new addition in Windows Server 2025 designed to enhance service account management and mitigate certain attack vectors.
Understanding dMSA and Its Intended Purpose
Delegated Managed Service Accounts (dMSAs) were introduced to address the security challenges associated with traditional service accounts. Historically, service accounts often utilized weak, reused passwords that were seldom rotated, making them attractive targets for attackers. dMSAs aim to eliminate the use of passwords in service accounts by binding them to machine identities, thereby enhancing security and simplifying management.
The BadSuccessor Attack Technique
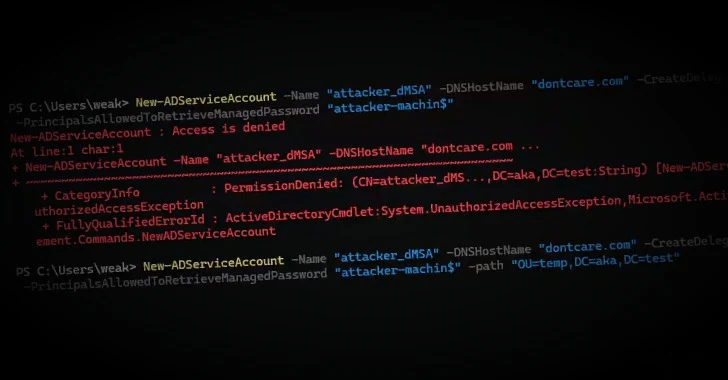
Security researchers at Akamai have uncovered an attack method, dubbed BadSuccessor, which exploits the dMSA feature to achieve privilege escalation within Active Directory. The attack leverages the migration process from traditional service accounts to dMSAs. During this process, dMSAs inherit the security identifiers (SIDs) and permissions of the accounts they replace. By manipulating this migration mechanism, an attacker can simulate the migration of any user account, including those with administrative privileges, to a dMSA under their control. This effectively grants the attacker the same permissions as the original user, compromising the entire domain.
Technical Details of the Exploit
The vulnerability arises during the Kerberos authentication phase of the dMSA migration. The Privilege Attribute Certificate (PAC) embedded in the ticket-granting ticket (TGT) issued by the Key Distribution Center (KDC) includes the SIDs of both the dMSA and the superseded service account, along with all associated groups. This transfer of permissions allows an attacker with write permissions over a dMSA’s attributes to mark it as a successor to any user account. Consequently, the KDC assumes a legitimate migration has occurred and grants the dMSA all the permissions of the original user.
Implications for Organizations
This vulnerability poses a significant risk to organizations relying on Active Directory for identity and access management. An attacker exploiting this flaw can escalate privileges, access sensitive data, and potentially disrupt critical services. The widespread use of Active Directory means that a successful exploit could have far-reaching consequences across an organization’s network.
Microsoft’s Response and Mitigation Measures
Akamai reported the vulnerability to Microsoft on April 1, 2025. Microsoft has classified the issue as moderate in severity, noting that successful exploitation requires specific permissions on the dMSA object, indicating an elevation of privileges. While a patch is currently in development, there is no immediate fix available.
In the interim, organizations are advised to:
– Restrict dMSA Creation: Limit the ability to create dMSAs to trusted administrators only. This reduces the risk of unauthorized dMSA creation and potential exploitation.
– Harden Permissions: Review and tighten permissions on dMSA objects and related attributes. Ensure that only necessary personnel have write access to these attributes.
– Monitor for Unauthorized Changes: Implement monitoring to detect unauthorized changes to dMSA configurations and migrations. Promptly investigate and remediate any suspicious activity.
Broader Context of Windows Server Vulnerabilities
This discovery adds to a series of critical vulnerabilities identified in Windows Server environments. For instance, in January 2025, Microsoft addressed multiple zero-day vulnerabilities, including:
– CVE-2025-21298: A remote code execution vulnerability in Windows Object Linking and Embedding (OLE) with a CVSS score of 9.8, affecting all supported Windows versions. This flaw allows unauthenticated attackers to execute arbitrary code via specially crafted emails.
– CVE-2025-21311: An elevation-of-privilege vulnerability in Windows NTLM V1, also with a CVSS score of 9.8, affecting Windows 11, Windows Server 2022, and Windows Server 2025. Exploitation can grant attackers system-level privileges without user interaction.
These vulnerabilities underscore the importance of timely patching and vigilant security practices within organizations.
Conclusion
The BadSuccessor vulnerability in Windows Server 2025’s dMSA feature highlights the complexities and potential risks associated with new security features. While dMSAs were designed to enhance security by eliminating password-based service accounts, this flaw demonstrates how attackers can exploit migration processes to escalate privileges. Organizations must proactively implement mitigation measures, restrict dMSA creation, and monitor for unauthorized changes to safeguard their Active Directory environments. Staying informed about emerging vulnerabilities and applying patches promptly remain critical components of a robust cybersecurity strategy.