In recent months, Russian businesses have faced a significant increase in cyberattacks involving the PureRAT malware. According to cybersecurity firm Kaspersky, these attacks have quadrupled in the first third of 2025 compared to the same period in 2024. The campaign, which began in March 2023, employs sophisticated phishing tactics to infiltrate systems and deploy a suite of malicious tools.
Attack Methodology
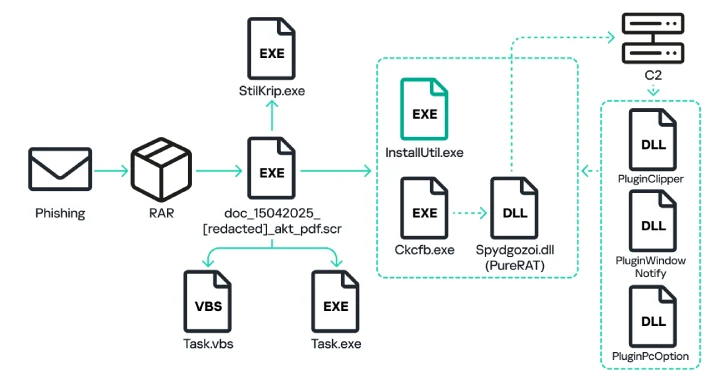
The attack sequence typically starts with a phishing email containing a RAR file attachment or a link to such an archive. These archives are cleverly disguised as legitimate Microsoft Word or PDF documents by using double extensions, such as doc_054_[redacted].pdf.rar. Once the recipient opens the archive and executes the contained file, the malware initiates a multi-stage infection process.
Upon execution, the initial file copies itself to the %AppData% directory under the name task.exe and creates a Visual Basic Script (VBS) named Task.vbs in the Startup folder to ensure persistence. This executable then unpacks another file, ckcfb.exe, which utilizes the system utility InstallUtil.exe to inject a decrypted module into the system. Subsequently, ckcfb.exe extracts and decrypts a DLL file named Spydgozoi.dll, which contains the core PureRAT payload.
PureRAT Capabilities
Once active, PureRAT establishes a secure SSL connection with a command-and-control (C2) server and transmits detailed system information, including antivirus software details, computer name, and system uptime. The C2 server can then deploy additional modules to execute various malicious activities:
– PluginPcOption: Executes commands for self-deletion, restarting the executable, and shutting down or rebooting the computer.
– PluginWindowNotify: Monitors active window titles for keywords like password, bank, or WhatsApp, enabling actions such as unauthorized fund transfers.
– PluginClipper: Functions as a clipper malware by replacing cryptocurrency wallet addresses copied to the clipboard with those controlled by the attacker.
Additionally, PureRAT includes modules that allow for downloading and executing arbitrary files, providing full access to the file system, registry, processes, camera, and microphone. It also implements keylogging functionality and enables remote desktop control, granting attackers comprehensive control over the infected system.
Deployment of PureLogs
Simultaneously, the initial executable extracts another binary named StilKrip.exe, identified as PureCrypter—a commercially available downloader active since 2022. PureCrypter downloads a file named Bghwwhmlr.wav, which follows a similar attack sequence to execute InstallUtil.exe and ultimately launch Ttcxxewxtly.exe. This executable unpacks and runs a DLL payload called PureLogs (Bftvbho.dll).
PureLogs is an off-the-shelf information stealer capable of harvesting data from web browsers, email clients, VPN services, messaging apps, wallet browser extensions, password managers, cryptocurrency wallet applications, and other programs like FileZilla and WinSCP.
Implications and Recommendations
The combination of PureRAT and PureLogs provides attackers with extensive access to infected systems and sensitive organizational data. The primary attack vector remains phishing emails with malicious attachments or links.
To mitigate the risk of such attacks, organizations should implement the following measures:
1. Employee Training: Educate staff on recognizing phishing attempts and the dangers of opening suspicious attachments or links.
2. Email Filtering: Deploy advanced email filtering solutions to detect and block phishing emails before they reach end-users.
3. Endpoint Protection: Utilize comprehensive endpoint detection and response (EDR) solutions to identify and neutralize malware threats.
4. Regular Updates: Ensure all systems and software are up-to-date with the latest security patches to prevent exploitation of known vulnerabilities.
5. Access Controls: Implement strict access controls and monitor user activities to detect unauthorized actions promptly.
By adopting these proactive measures, organizations can enhance their defenses against sophisticated malware campaigns like those involving PureRAT and PureLogs.