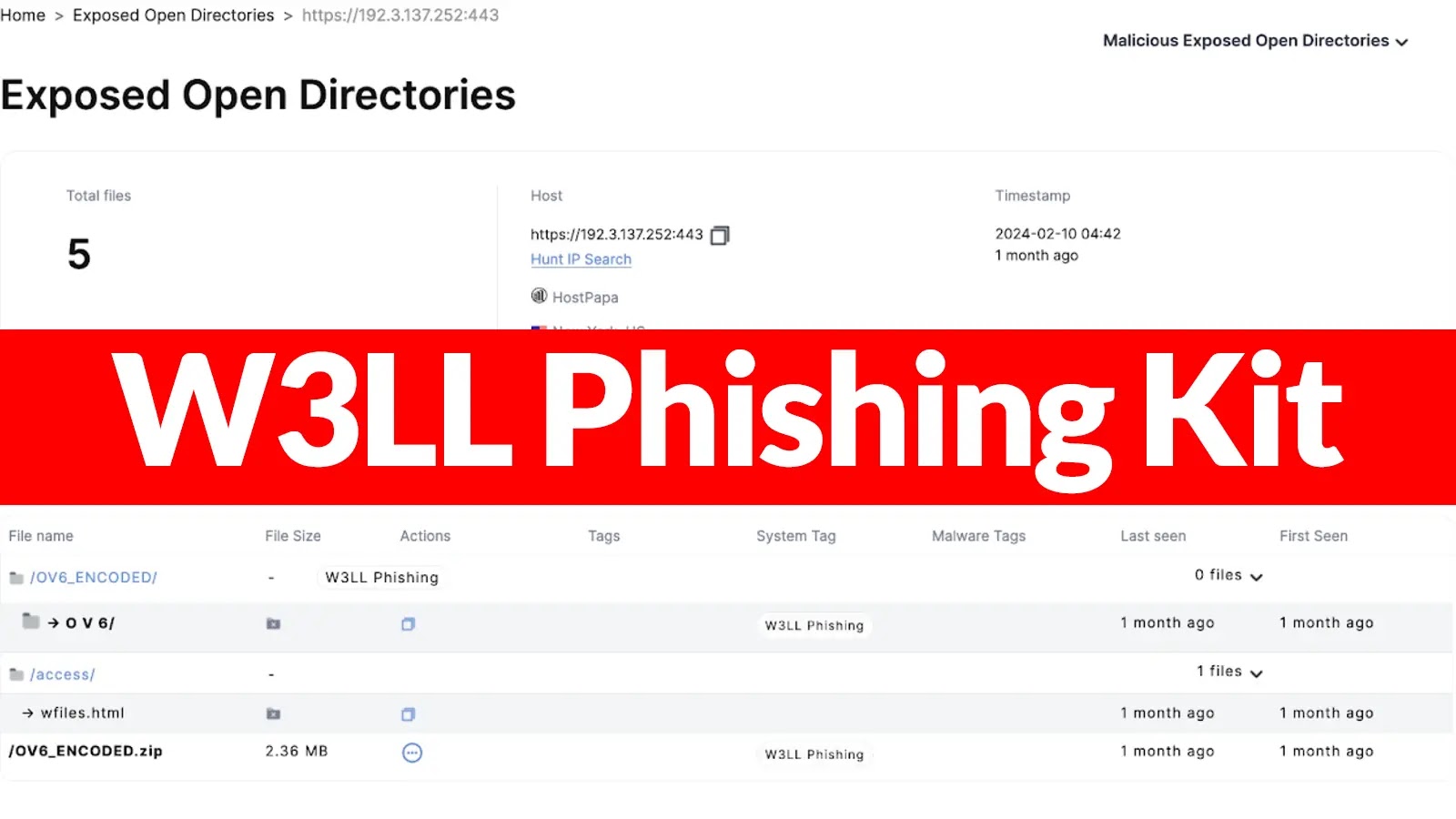
In the ever-evolving landscape of cyber threats, a particularly insidious tool has emerged, posing significant risks to Microsoft 365 users. The W3LL Phishing Kit, first identified by cybersecurity firm Group-IB in 2022, has been actively deployed in campaigns aimed at harvesting Outlook login credentials through elaborate impersonation techniques.
The Emergence of W3LL Phishing Kit
The W3LL Phishing Kit is a comprehensive phishing-as-a-service (PhaaS) tool that has evolved into a full-fledged ecosystem. It features its own underground marketplace, known as the W3LL Store, where cybercriminals can customize and purchase various tools tailored to their malicious campaigns. This marketplace caters to a closed community of at least 500 threat actors, offering a suite of 16 custom tools designed for business email compromise (BEC) attacks. ([thehackernews.com](https://thehackernews.com/2023/09/w3ll-store-how-secret-phishing.html?utm_source=openai))
Targeting Microsoft 365 Credentials
The primary objective of the W3LL Phishing Kit is to harvest Microsoft 365 credentials. It employs adversary-in-the-middle (AitM) techniques, allowing attackers to intercept session cookies and effectively bypass multi-factor authentication (MFA) mechanisms. This method significantly increases the success rate of credential theft, even against accounts fortified with additional security layers. ([duo.com](https://duo.com/decipher/w3ll-threat-actor-built-a-microsoft-365-phishing-ecosystem?utm_source=openai))
Anatomy of the Phishing Campaign
The attack typically begins with a meticulously crafted email that directs recipients to a phishing page designed to mimic legitimate services, such as Adobe’s Shared File platform. Unsuspecting users are prompted to log in to access a purportedly shared document. Upon entering their credentials, the information is transmitted to attacker-controlled servers, granting unauthorized access to the victim’s account.
Technical Sophistication and Obfuscation
The W3LL Phishing Kit employs advanced obfuscation techniques to evade detection and analysis. One notable method is the use of ionCube, an encryption tool for PHP code, which significantly hampers reverse engineering efforts. The kit’s configuration is managed through a config.php file containing crucial operational parameters, allowing attackers to customize various aspects of their campaigns, from the visual elements of phishing pages to the destination of stolen credentials.
Global Impact and Financial Implications
Between October 2022 and July 2023, the W3LL Phishing Kit was used to target over 56,000 corporate Microsoft 365 accounts, resulting in at least 8,000 successful compromises. The attacks primarily affected organizations in the United States, the United Kingdom, Australia, Germany, Canada, France, the Netherlands, Switzerland, and Italy. The sectors most impacted include manufacturing, IT, consulting, financial services, healthcare, and legal services. The financial losses attributed to these attacks are estimated to be in the hundreds of thousands, if not millions, of euros per victim. ([thehackernews.com](https://thehackernews.com/2023/09/w3ll-store-how-secret-phishing.html?utm_source=openai))
The W3LL Store: A Cybercriminal Marketplace
The W3LL Store operates as a clandestine marketplace, offering a range of tools and services to cybercriminals. In addition to the W3LL Phishing Kit, the store provides SMTP senders for bulk email spam, malicious link stagers, vulnerability scanners, and reconnaissance tools. The marketplace is structured to cater to cybercriminals of all technical skill levels, providing customer support, video tutorials, and a referral bonus program. This ecosystem enables threat actors to run highly effective BEC phishing campaigns with a high level of automation and scalability. ([scmagazine.com](https://www.scmagazine.com/news/w3ll-groups-phishing-tools-used-to-target-56000-corporate-microsoft-365-accounts?utm_source=openai))
Bypassing Multi-Factor Authentication
One of the most concerning aspects of the W3LL Phishing Kit is its ability to bypass MFA protections. By employing AitM techniques, the kit intercepts session cookies during the authentication process, rendering MFA ineffective. This development underscores the need for organizations to adopt additional security measures beyond MFA to protect against such sophisticated attacks. ([duo.com](https://duo.com/decipher/w3ll-threat-actor-built-a-microsoft-365-phishing-ecosystem?utm_source=openai))
Recommendations for Mitigation
To defend against threats posed by the W3LL Phishing Kit, organizations should consider implementing the following measures:
1. Enhanced Email Filtering: Deploy advanced email filtering solutions to detect and block phishing emails before they reach end-users.
2. User Education and Awareness: Conduct regular training sessions to educate employees about the dangers of phishing attacks and how to recognize suspicious emails and links.
3. Behavioral Analytics: Utilize behavioral analytics tools to monitor for unusual login patterns or access behaviors that may indicate a compromised account.
4. Zero Trust Architecture: Implement a Zero Trust security model that requires continuous verification of user identity and device security posture, regardless of location.
5. Regular Security Audits: Perform regular security audits and penetration testing to identify and remediate vulnerabilities within the organization’s infrastructure.
Conclusion
The W3LL Phishing Kit represents a significant advancement in the capabilities of cybercriminals to conduct large-scale, sophisticated phishing campaigns. Its ability to bypass MFA and its comprehensive suite of tools make it a formidable threat to organizations worldwide. By understanding the mechanics of such attacks and implementing robust security measures, organizations can better protect themselves against these evolving threats.