ASUS has recently released critical updates to rectify two significant security vulnerabilities in its DriverHub software, which, if exploited, could allow attackers to execute arbitrary code remotely on affected systems.
Overview of ASUS DriverHub
DriverHub is a utility developed by ASUS to streamline the process of identifying and updating motherboard drivers. By detecting the motherboard model, it connects to a dedicated server at driverhub.asus[.]com to fetch and install the necessary driver updates.
Details of the Vulnerabilities
The identified vulnerabilities are as follows:
1. CVE-2025-3462: This vulnerability, with a CVSS score of 8.4, is categorized as an origin validation error. It allows unauthorized entities to interact with DriverHub’s features through specially crafted HTTP requests.
2. CVE-2025-3463: With a higher CVSS score of 9.4, this flaw pertains to improper certificate validation. It enables untrusted sources to influence system behavior via malicious HTTP requests.
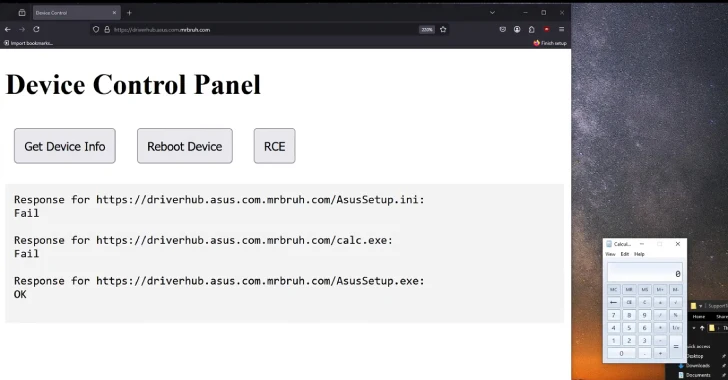
Security researcher MrBruh, who discovered these vulnerabilities, highlighted that they could be exploited to achieve remote code execution through a single-click attack.
Exploitation Mechanism
The attack involves deceiving a user into visiting a sub-domain resembling driverhub.asus[.]com (e.g., driverhub.asus.com.
Upon execution, AsusSetup.exe reads from AsusSetup.ini, which contains metadata about the driver. When run with the -s flag (used by DriverHub for silent installations), it executes the command specified in the SilentInstallRun property of the INI file. An attacker can manipulate this property to run arbitrary code.
To execute this exploit, an attacker needs to set up a domain hosting three files:
1. The malicious payload intended for execution.
2. A modified AsusSetup.ini file with the SilentInstallRun property pointing to the malicious payload.
3. The legitimate AsusSetup.exe binary.
By directing the user to this malicious domain, the attacker can initiate the execution of the payload through DriverHub.
ASUS’s Response and Recommendations
Following responsible disclosure on April 8, 2025, ASUS addressed these issues by releasing patches on May 9, 2025. The company has not reported any instances of these vulnerabilities being exploited in the wild.
ASUS strongly advises all users to update their DriverHub installations to the latest version. Users can do this by opening ASUS DriverHub and clicking the Update Now button.
Historical Context of ASUS Security Incidents
This is not the first time ASUS has faced security challenges. In 2018, the company dealt with elevation of privilege vulnerabilities in its drivers, which could allow local attackers to gain higher system privileges. Additionally, in 2019, ASUS’s Live Update utility was compromised, leading to the distribution of backdoored software updates to users. These incidents underscore the importance of timely software updates and vigilant security practices.
Conclusion
The recent vulnerabilities in ASUS DriverHub highlight the critical need for robust security measures in software utilities. Users are urged to promptly update their software to mitigate potential risks. Regular software updates and adherence to security best practices are essential in safeguarding systems against emerging threats.