A sophisticated cyber espionage campaign has been uncovered, revealing that a China-aligned advanced persistent threat (APT) group, known as TheWizards, is leveraging a tool named Spellbinder to conduct adversary-in-the-middle (AitM) attacks. This technique exploits the IPv6 Stateless Address Autoconfiguration (SLAAC) protocol to facilitate lateral movement within compromised networks, enabling the interception and redirection of legitimate software traffic to malicious servers controlled by the attackers.
Understanding the Attack Mechanism
The Spellbinder tool capitalizes on the IPv6 SLAAC protocol, which allows devices on a network to automatically configure their own IP addresses without the need for a central server. By spoofing Router Advertisement (RA) messages, Spellbinder can deceive devices into adopting the attacker’s machine as their default gateway. This manipulation enables the interception of network traffic, allowing the attackers to redirect legitimate software update requests to malicious servers.
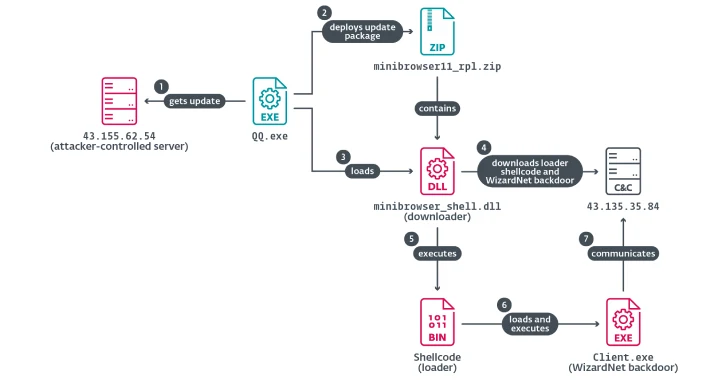
In this campaign, the attackers specifically targeted the software update mechanisms of popular Chinese applications, such as Sogou Pinyin and Tencent QQ. By hijacking these processes, they delivered a malicious downloader that subsequently installed a modular backdoor named WizardNet on the compromised systems.
The Role of Spellbinder in the Attack Chain
The initial phase of the attack involves delivering a ZIP archive containing four files: AVGApplicationFrameHost.exe, wsc.dll, log.dat, and winpcap.exe. Upon execution, the attackers install winpcap.exe and run AVGApplicationFrameHost.exe, which is exploited to sideload the malicious wsc.dll file. This DLL reads shellcode from log.dat and executes it in memory, thereby launching the Spellbinder tool.
Spellbinder utilizes the WinPcap library to capture and manipulate network packets. By exploiting IPv6’s Network Discovery Protocol, it sends spoofed ICMPv6 Router Advertisement messages, tricking devices into recognizing the attacker’s machine as a legitimate router. This allows the attackers to intercept and redirect traffic, particularly targeting software update requests.
Hijacking Software Update Mechanisms
In one observed instance from 2024, the attackers intercepted the DNS query for Tencent QQ’s update domain (update.browser.qq[.]com) and responded with the IP address of a malicious server (43.155.62[.]54). This server hosted a trojanized version of the software update, which, when executed, deployed the WizardNet backdoor. This backdoor is modular, capable of receiving and executing .NET payloads on the infected host, thereby granting the attackers extensive control over the compromised system.
Broader Implications and Related Threats
TheWizards APT group has been active since at least 2022, targeting individuals and organizations within the gambling sectors across Cambodia, Hong Kong, Mainland China, the Philippines, and the United Arab Emirates. Their use of advanced tools like Spellbinder and WizardNet underscores the evolving sophistication of state-sponsored cyber threats.
This campaign is part of a broader trend where Chinese state-sponsored hackers exploit vulnerabilities in widely used software to conduct espionage and data exfiltration. For instance, in September 2024, it was reported that Chinese hackers infiltrated U.S. internet service providers as part of a cyber espionage campaign aimed at gathering sensitive information. These activities highlight the persistent and evolving nature of cyber threats emanating from state-sponsored actors.
Mitigation Strategies and Recommendations
To defend against such sophisticated attacks, organizations should consider implementing the following measures:
1. Disable Unused Protocols: If IPv6 is not in use within the network, it should be disabled to prevent exploitation of its features by malicious actors.
2. Monitor Network Traffic: Regularly inspect network traffic for unusual patterns or unauthorized devices acting as routers, which could indicate the presence of spoofed RA messages.
3. Implement RA Guard: Deploy Router Advertisement Guard features on network switches to filter out unauthorized RA messages and prevent devices from accepting malicious router advertisements.
4. Secure Software Update Mechanisms: Ensure that software updates are obtained from verified sources and that update mechanisms are secured against hijacking attempts.
5. Educate Users: Provide training to users about the risks associated with software updates and the importance of verifying update sources before installation.
By adopting these strategies, organizations can enhance their resilience against adversary-in-the-middle attacks and other sophisticated cyber threats.