In today’s digital landscape, social engineering has emerged as a predominant threat, exploiting human psychology to bypass sophisticated technical defenses. Chief Information Security Officers (CISOs) and Security Operations Center (SOC) leaders are at the forefront of this battle, tasked with fortifying their organizations against such deceptive tactics.
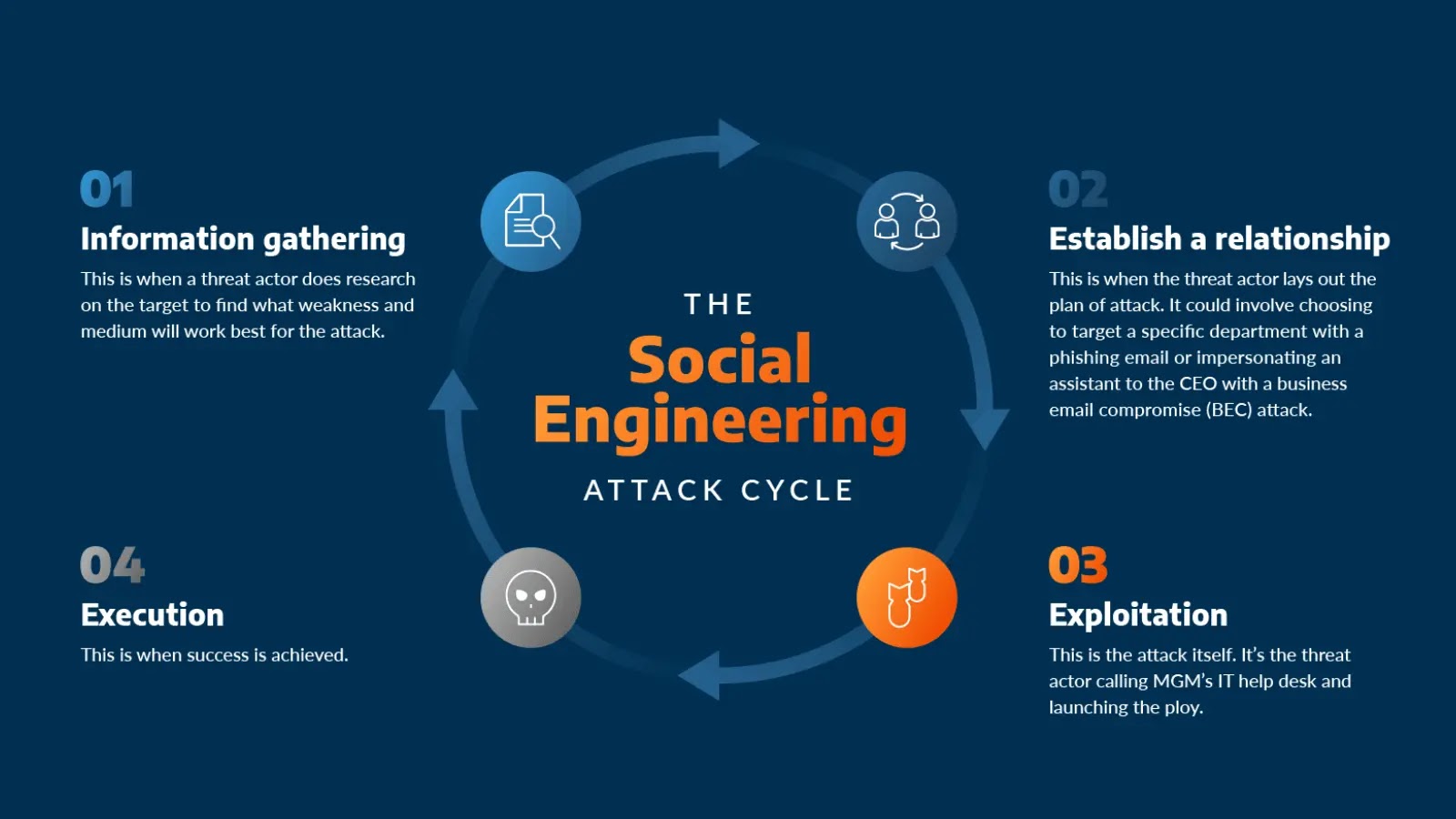
Understanding Social Engineering
Social engineering involves manipulating individuals into divulging confidential information or performing actions that compromise security. Techniques such as phishing, pretexting, baiting, and scareware are commonly employed to exploit human vulnerabilities. The success of these attacks hinges on psychological manipulation, leveraging trust, authority, urgency, and curiosity to deceive targets.
The Escalating Threat Landscape
Recent data underscores the growing prevalence of social engineering attacks:
– A staggering 92% of organizations experienced credential compromises due to email-based social engineering in 2023, with an average of six incidents per organization. ([infosecurity-magazine.com](https://www.infosecurity-magazine.com/news/credential-compromise-social/?utm_source=openai))
– Social engineering incidents have nearly doubled, now accounting for 17% of all breaches. ([nationalcybersecurity.com](https://nationalcybersecurity.com/social-engineering-gains-lead-to-spiraling-breach-costs-hacking-cybersecurity-infosec-comptia-pentest-ransomware/?utm_source=openai))
– A significant 68% of data breaches are attributed to social engineering tactics. ([cybernoz.com](https://cybernoz.com/68-of-data-breach-occurs-due-to-social-engineering-attacks/?utm_source=openai))
These statistics highlight the critical need for organizations to prioritize defenses against social engineering.
The Role of Artificial Intelligence in Social Engineering
Artificial Intelligence (AI) has transformed the landscape of social engineering:
– Enhanced Attack Sophistication: AI enables attackers to craft highly personalized and convincing phishing messages by analyzing a target’s communication patterns and online behavior. ([prnewswire.com](https://www.prnewswire.com/news-releases/new-ninjio-report-provides-insights-on-rapidly-growing-threat-of-ai-powered-social-engineering-302176177.html?utm_source=openai))
– Defensive Applications: Conversely, AI can bolster defenses by detecting anomalies in user behavior and identifying potential social engineering attempts.
This dynamic underscores the necessity for continuous investment in both technological solutions and employee training.
Technical Defenses Against Social Engineering
While human factors are central to social engineering, implementing robust technical controls is essential:
– Email Security: Deploy advanced email filtering solutions to detect and block phishing attempts.
– Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security, making unauthorized access more challenging.
– Regular Software Updates: Ensure all systems are up-to-date to mitigate vulnerabilities that could be exploited.
– User Behavior Analytics: Utilize tools that monitor and analyze user behavior to detect anomalies indicative of compromised accounts.
Building a Culture of Security Awareness
Technical measures alone are insufficient without a strong culture of security awareness:
– Comprehensive Training Programs: Develop and implement regular training sessions to educate employees on recognizing and responding to social engineering attempts.
– Simulated Phishing Exercises: Conduct regular simulations to test employee responses and reinforce training.
– Clear Reporting Channels: Establish and communicate clear procedures for reporting suspected social engineering attempts.
– Leadership Engagement: Ensure that organizational leaders actively participate in and promote security initiatives.
Incident Response Planning
Despite preventive measures, incidents may still occur. Having a robust incident response plan is crucial:
– Defined Roles and Responsibilities: Clearly outline the roles and responsibilities of team members during an incident.
– Communication Protocols: Establish protocols for internal and external communication during and after an incident.
– Post-Incident Analysis: Conduct thorough analyses to identify root causes and implement corrective actions.
Conclusion
Social engineering poses a significant and evolving threat to organizations. CISOs and SOC leaders must adopt a multifaceted approach that combines technical defenses, continuous employee education, and a proactive security culture to effectively mitigate these risks.