In a recent wave of cyberattacks, Russian threat actors have been exploiting legitimate Microsoft OAuth 2.0 authentication workflows to infiltrate targeted organizations. Since early March 2025, these sophisticated campaigns have primarily focused on individuals and entities associated with Ukraine and human rights initiatives.
Social Engineering Tactics
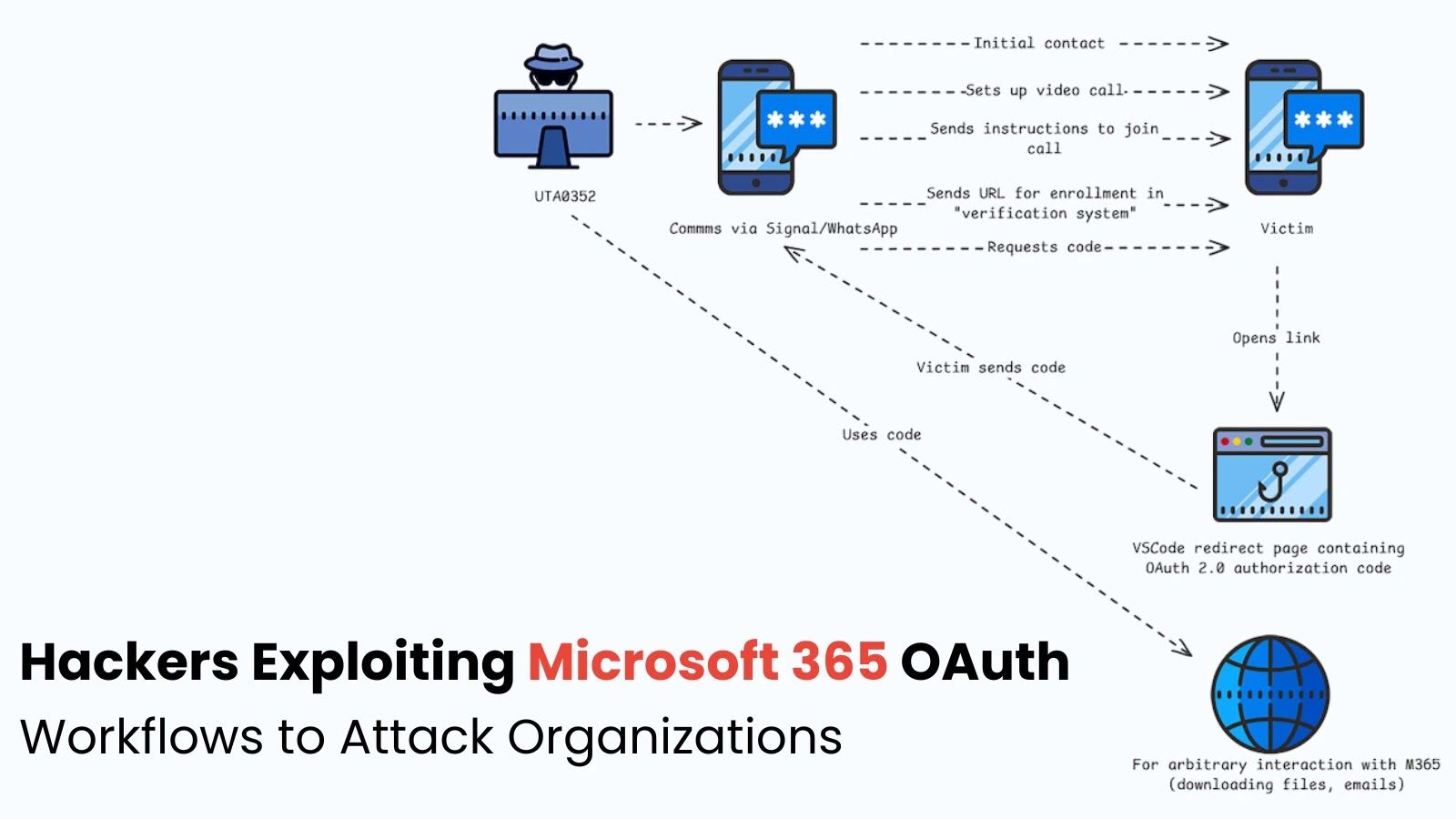
The attackers, identified as UTA0352 and UTA0355, have demonstrated advanced social engineering capabilities aimed at unauthorized access to Microsoft 365 accounts. Unlike traditional phishing methods, these operations leverage Microsoft’s official infrastructure, significantly complicating detection efforts.
Volexity researchers highlighted that these recent campaigns benefit from all user interactions taking place on Microsoft’s official infrastructure; there is no attacker-hosted infrastructure used in these attacks.
Primary targets include non-governmental organizations supporting human rights, think tanks, and groups providing humanitarian aid to Ukraine. These organizations are particularly vulnerable due to limited resources and staffing, making them susceptible to sophisticated social engineering tactics.
Exploiting Trust in Microsoft Services
The attack sequence begins with the perpetrators contacting victims through secure messaging platforms like Signal and WhatsApp, posing as officials from European countries such as Ukraine, Bulgaria, Romania, and Poland. In one notable instance, they utilized a compromised Ukrainian government account to establish credibility.
Victims are invited to participate in supposed video conferences or private meetings with European political figures to discuss Ukraine-related issues. During these interactions, they receive malicious Microsoft login URLs that generate OAuth authorization codes upon clicking.
Volexity explains, If the victim shares the OAuth code, the attacker is then able to generate an access token that ultimately allows access to the victim’s M365 account.
This method is particularly effective because it exploits legitimate Microsoft authentication workflows. When victims click the provided links, they are directed to official Microsoft pages, avoiding the typical red flags associated with phishing sites.
In some cases, attackers use the stolen OAuth authorization code to permanently register new devices to the victim’s Microsoft Entra ID (formerly Azure AD), ensuring persistent access to compromised accounts.
Post-compromise activities include downloading victims’ emails and accessing other sensitive account data. Attackers further obfuscate their actions by routing activities through proxy networks geolocated to match the victim’s location, complicating detection efforts.
Recommendations for Mitigation
To defend against such sophisticated attacks, organizations should:
– User Training: Educate users to be cautious of unsolicited contacts via secure messaging apps, especially those requesting code sharing or URL information.
– Conditional Access Policies: Implement policies that restrict access to only approved devices, reducing the risk of unauthorized access.
Volexity attributes these campaigns to Russian threat actors with medium confidence, noting that all messages were themed around Ukraine and targeted individuals historically of interest to Russian intelligence operations.
This series of attacks marks the second time since January 2025 that Russian actors have exploited Microsoft OAuth workflows to target organizations.