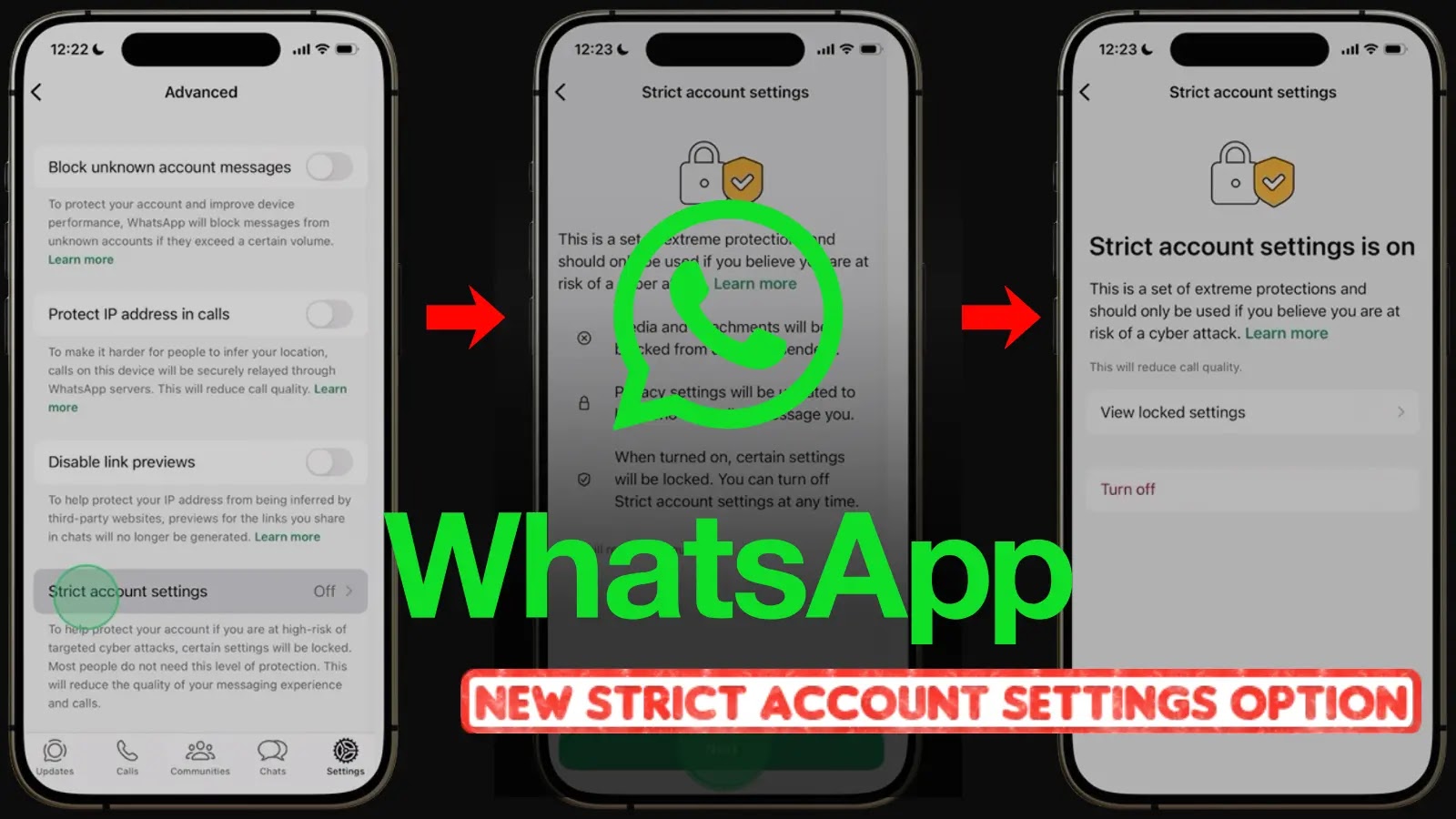
A recent phishing campaign, identified as PoisonSeed, has been exploiting vulnerabilities in customer relationship management (CRM) and bulk email services to target cryptocurrency users. This campaign employs a novel tactic where victims are provided with fraudulent crypto seed phrases, enabling attackers to access and steal their digital assets.
Understanding the PoisonSeed Campaign
The PoisonSeed campaign has been active for the past month, focusing on users of prominent cryptocurrency platforms such as Coinbase and Ledger. The attackers infiltrate CRM and bulk email providers—including Mailchimp, Hubspot, Mailgun, SendGrid, and Zoho—to distribute phishing emails that appear legitimate. These emails inform recipients that Coinbase is transitioning to self-custodial wallets and urge them to transfer their assets to new cryptocurrency wallets using provided seed phrases.
Unlike traditional phishing methods that embed malicious links, this campaign includes security seed phrases within the email content. When recipients use these seed phrases to create new wallets, attackers gain direct access to their funds. This method effectively bypasses conventional detection mechanisms, as the emails lack typical phishing indicators like suspicious links or attachments.
The Role of CRM and Bulk Email Services
By compromising accounts within CRM and bulk email services, attackers can send phishing emails from trusted domains, increasing the likelihood of recipients trusting the messages. For instance, in mid-March, Coinbase alerted users to such attacks, emphasizing the importance of never entering a recovery phrase received from an external source. Reports estimate that Coinbase users have collectively lost approximately $46 million worth of cryptocurrency due to phishing schemes.
Silent Push, a cyber intelligence firm, discovered that the phishing emails were sent from a compromised Akamai SendGrid account. This account was also used to send phishing messages aimed at compromising other organizations’ SendGrid accounts, suggesting a strategy to perpetuate the scam through additional bulk email accounts.
Broader Implications and Related Campaigns
The PoisonSeed campaign is part of a broader trend where attackers exploit legitimate services to conduct phishing attacks. For example, a sophisticated Facebook phishing campaign was observed exploiting a zero-day flaw in Salesforce’s email services. Threat actors crafted targeted phishing messages using Salesforce’s domain and infrastructure, evading conventional detection methods by combining the Salesforce vulnerability with legacy quirks in Facebook’s Web Games platform. These emails, appearing to come from Meta and sent from a @salesforce.com domain, directed users to rogue landing pages designed to capture account credentials and two-factor authentication codes. The phishing kit was hosted as a game under the Facebook apps platform, further enhancing its legitimacy. Salesforce addressed this zero-day vulnerability by implementing new checks to prevent the use of email addresses from the @salesforce.com domain.
In another instance, a credential phishing campaign utilized the legitimate SuperMailer newsletter distribution app. This campaign, which began with a handful of emails in January 2023, escalated to thousands by May 2023. The attackers exploited a coding error in SuperMailer, allowing them to link multiple different phishing emails to the same campaign. Techniques such as open redirects, varied senders, URL randomization, and reply chains were employed to bypass secure email gateways and reach users’ inboxes. The social engineering element involved requests for password details, a tactic that remains effective despite its simplicity.
Protective Measures and Recommendations
The increasing sophistication of phishing campaigns underscores the need for robust security measures. Organizations should implement multi-layered security strategies that combine technological solutions with employee training. Regular security awareness training can help employees recognize phishing attempts and understand the importance of not sharing sensitive information, such as recovery phrases, received from external sources.
Additionally, organizations should monitor and secure their CRM and bulk email service accounts to prevent unauthorized access. Implementing strong authentication methods, such as multi-factor authentication, can add an extra layer of security. Regular audits and updates to security protocols can also help identify and mitigate potential vulnerabilities.
In conclusion, the PoisonSeed campaign highlights the evolving tactics of cybercriminals who exploit trusted platforms to execute phishing attacks. By understanding these methods and implementing comprehensive security measures, organizations and individuals can better protect themselves against such threats.