Apple’s forthcoming A19 chip is poised to rival Qualcomm’s Snapdragon 8 Elite 2 in performance, yet the company appears to prioritize energy efficiency over sheer […]
Month: June 2025
OpenAI’s Promotional Video with Jony Ive Removed Amid Trademark Dispute
OpenAI has recently taken down a nine-minute promotional video featuring Jony Ive and CEO Sam Altman due to a trademark dispute concerning the name io. […]
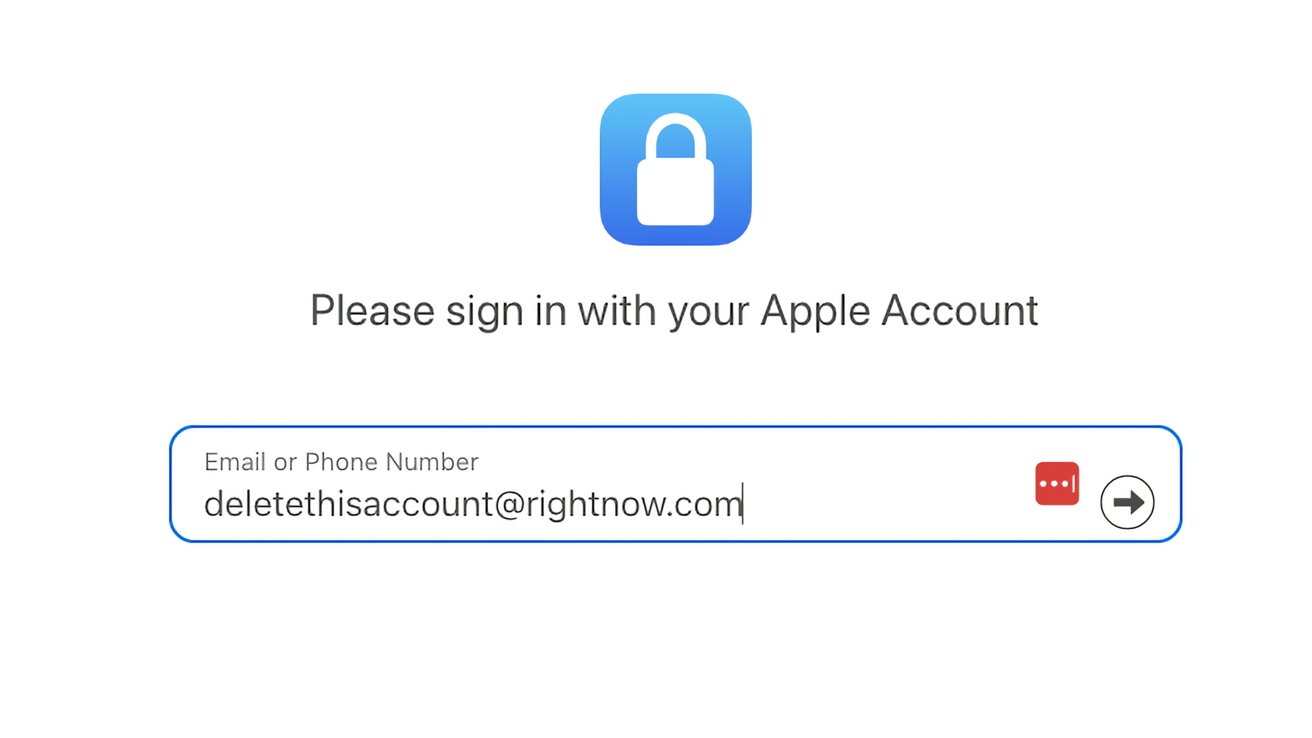
Comprehensive Guide to Deleting or Deactivating Your Apple ID Account
Your Apple ID serves as the gateway to a multitude of Apple services, including the App Store, iCloud, Apple Music, and more. However, there may […]
Apple’s App Store Under EU Scrutiny: Potential Changes to Avoid Hefty Fines
Apple Inc. is currently engaged in critical negotiations with the European Union (EU) to address concerns regarding its App Store practices. This move aims to […]
iPadOS 26: Transforming the iPad into a Productivity Powerhouse
Apple’s iPadOS 26 marks a significant evolution in the iPad’s journey, introducing features that bridge the gap between tablet and desktop computing. This update enhances […]
[June-23-2025] Daily Cybersecurity Threat Report
I. Executive Summary The past 24 hours have seen a dynamic and concerning cybersecurity landscape, primarily shaped by escalating geopolitical tensions, particularly those linked to […]
Critical Vulnerability in Apache SeaTunnel Allows Unauthenticated File Access and Remote Code Execution
Apache SeaTunnel, a widely adopted distributed data integration platform, has recently disclosed a significant security vulnerability identified as CVE-2025-32896. This flaw permits unauthenticated attackers to […]
Sophisticated Phishing Campaign Exploits Government Domains to Target TxTag Users
A recent phishing campaign has emerged, targeting individuals with fraudulent toll payment notices purportedly from TxTag, the Texas toll collection system. This scheme employs advanced […]
Cybercriminals Exploit Vercel Hosting Platform to Distribute Remote Access Malware
In a concerning development, cybercriminals have begun exploiting Vercel, a reputable frontend hosting platform, to disseminate remote access malware. By leveraging Vercel’s infrastructure, attackers are […]
Critical Template Injection Vulnerability in Insomnia API Client Enables Arbitrary Code Execution
A critical security flaw has been identified in the Insomnia API Client, a widely-used tool for API testing and development. This vulnerability, designated as CVE-2025-1087 […]


![[June-23-2025] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)



