As artificial intelligence (AI) becomes increasingly integrated into critical sectors such as healthcare, finance, and cybersecurity, the need for robust security measures tailored to AI […]
Month: June 2025
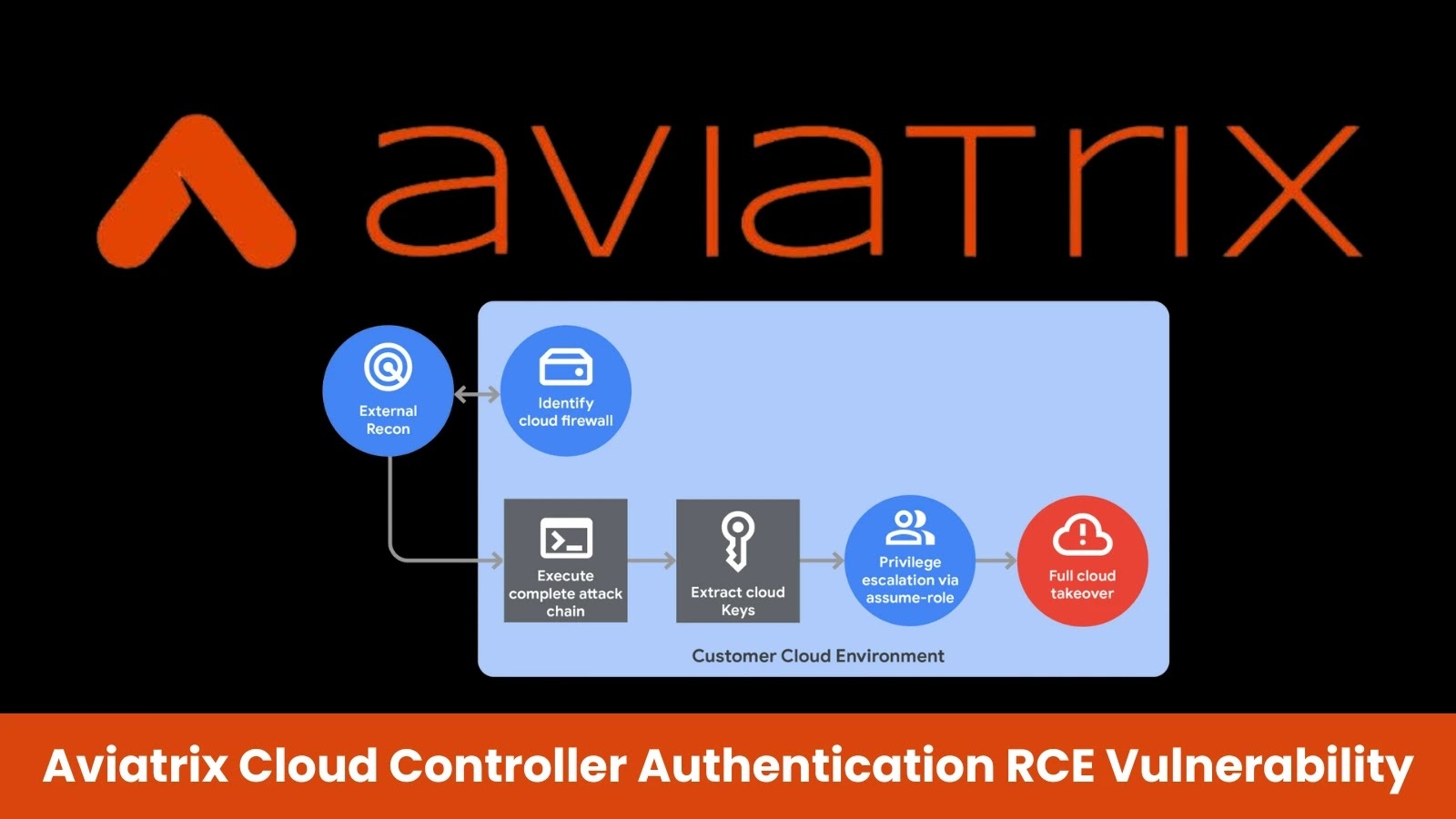
Critical Vulnerabilities in Aviatrix Controller Pose Severe Risks to Cloud Environments
Recent discoveries have unveiled two critical vulnerabilities in the Aviatrix Controller, a pivotal component in cloud networking that facilitates connectivity across various vendors and regions. […]
Sophisticated DMV-Themed Phishing Campaign Targets U.S. Citizens
In May 2025, a sophisticated phishing campaign emerged, targeting U.S. citizens by impersonating state Department of Motor Vehicles (DMV) agencies. This large-scale operation combined SMS […]
Critical Vulnerability in Xiaomi’s Interoperability App Exposes Devices to Unauthorized Access
A significant security flaw has been identified in Xiaomi’s Interoperability Application, potentially compromising millions of devices worldwide. This vulnerability, designated as CVE-2024-45347, has been assigned […]
OPPO Clone Phone Vulnerability Exposes User Data via Weak Wi-Fi Hotspot Security
A significant security vulnerability has been identified in OPPO’s Clone Phone feature, potentially exposing sensitive user data through inadequately secured Wi-Fi hotspots. This flaw, designated […]
Pro-Iranian Hacktivists Escalate Cyber Attacks on U.S. Networks Amid Rising Tensions
The Department of Homeland Security (DHS) has issued a critical advisory highlighting an escalating cyber threat from pro-Iranian hacktivist groups targeting United States networks. This […]
Malicious Apps Exploit Photo Libraries to Steal Cryptocurrency Data
In a significant cybersecurity breach, malicious applications have infiltrated both Apple’s App Store and Google’s Play Store, compromising user data by exploiting access to photo […]
Prometei Botnet Resurges with Enhanced Capabilities and Global Reach
The Prometei botnet, a sophisticated and modular malware system, has experienced a significant resurgence since March 2025, as reported by Palo Alto Networks. This resurgence […]
Echo Chamber: A New Method to Bypass AI Safeguards in Large Language Models
Recent advancements in artificial intelligence have led to the widespread adoption of Large Language Models (LLMs) like OpenAI’s ChatGPT and Google’s Bard. These models are […]
China-Linked Salt Typhoon Exploits Cisco Vulnerability to Target Canadian Telecom
In a recent cybersecurity development, the Canadian Centre for Cyber Security and the U.S. Federal Bureau of Investigation (FBI) have jointly issued an advisory concerning […]