Apple’s Photos app serves as the central hub for storing, organizing, and editing your images and videos across iPhone, iPad, and Mac devices. This guide […]
Month: June 2025
Anticipating iOS 26: Developer Beta Updates and Public Beta Release Timeline
Apple’s iOS 26, unveiled at the Worldwide Developers Conference (WWDC) on June 9, 2025, introduces a significant overhaul to the iPhone operating system. This update […]
Automakers Resist Apple’s CarPlay Ultra, Citing Overreach and Data Concerns
Apple’s introduction of CarPlay Ultra, an advanced iteration of its in-car software, has been met with resistance from several major automakers. This new system extends […]
Apple’s M5 iPad Pro with OLED Display Set for Fall 2025 Release as Screen Production Begins
Apple is gearing up for the release of its next-generation iPad Pro, featuring the powerful M5 chip and an advanced OLED display. Recent reports indicate […]
Echo Chamber Attack: A New Threat to AI Model Security
In the rapidly evolving landscape of artificial intelligence, ensuring the safety and reliability of Large Language Models (LLMs) has become paramount. Recent research has unveiled […]
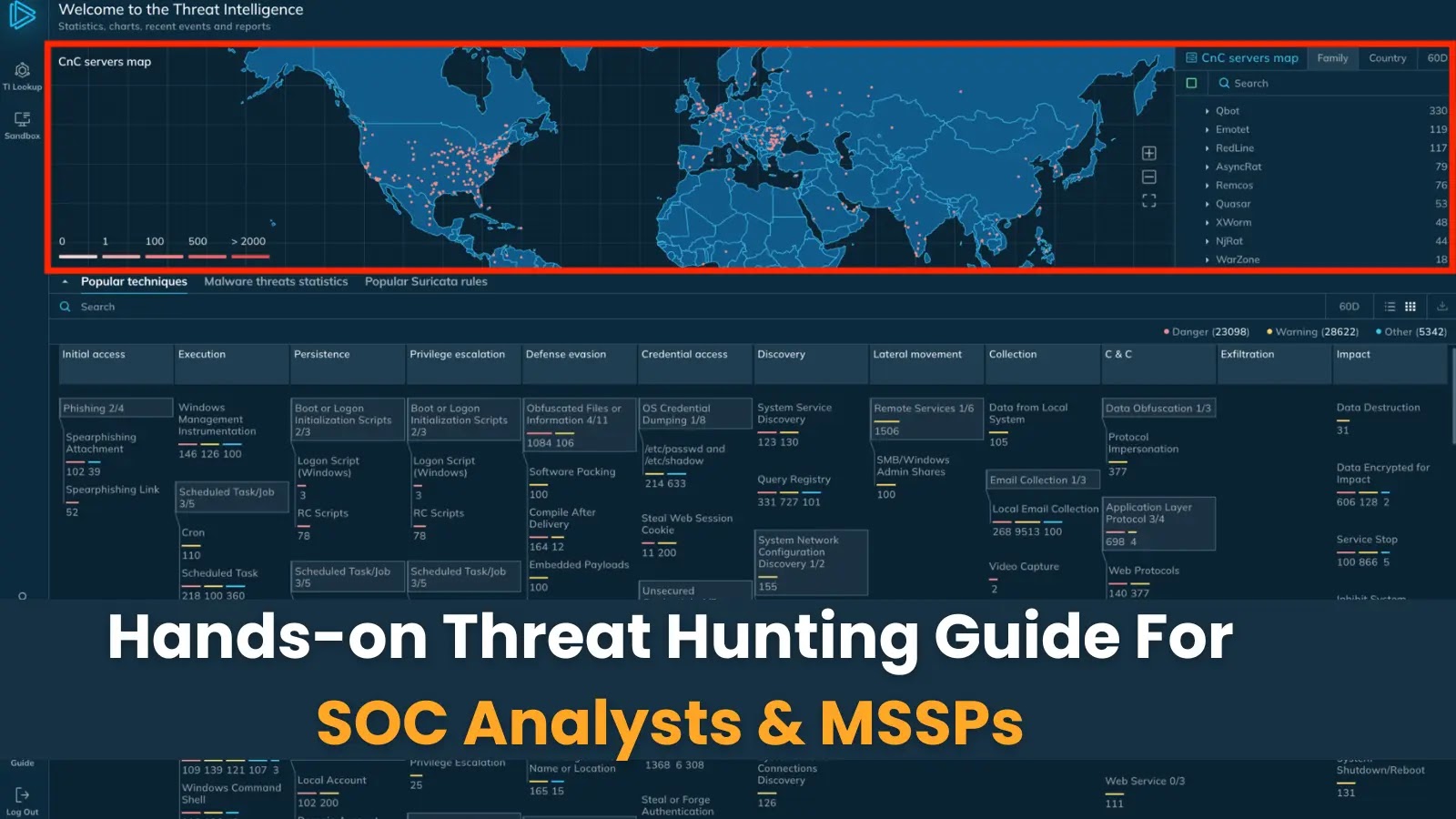
Hands-On Cybersecurity Threat Hunting Guide for SOC Analysts and MSSPs
In the ever-evolving landscape of cyber threats, Security Operations Center (SOC) analysts and Managed Security Service Providers (MSSPs) must adopt proactive threat-hunting strategies to stay […]
McLaren Health Care Data Breach Exposes Personal Information of 743,000 Individuals
McLaren Health Care, a prominent healthcare provider headquartered in Grand Blanc, Michigan, has reported a significant data breach that compromised the personal information of 743,131 […]
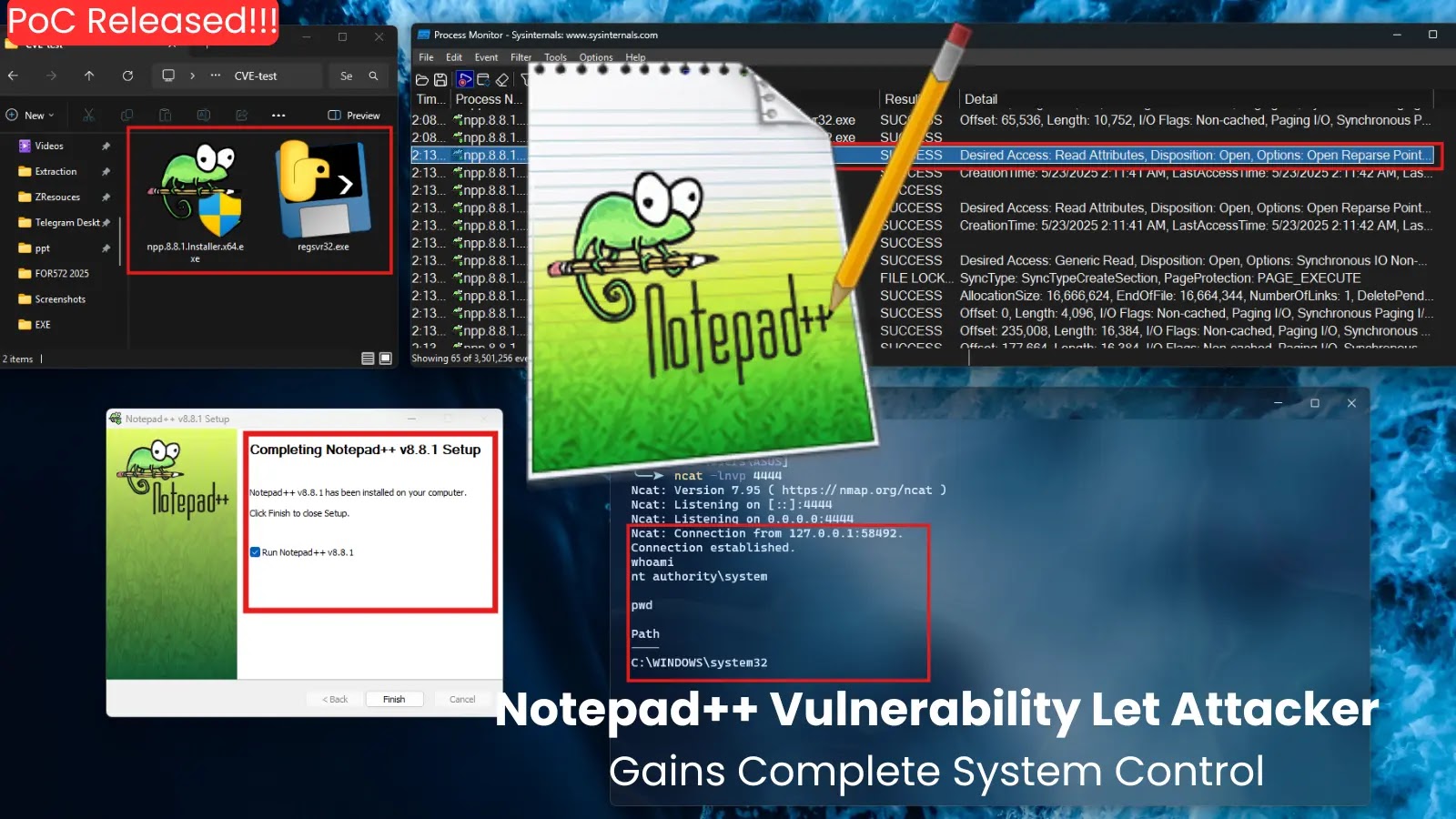
Critical Notepad++ Vulnerability Exposes Systems to Full Compromise
A critical security vulnerability has been identified in Notepad++ version 8.8.1, potentially allowing attackers to gain complete control over affected systems. This flaw, designated as […]
China-Linked ‘LapDogs’ Cyber Espionage Campaign Exploits Over 1,000 SOHO Devices
A sophisticated cyber espionage campaign, attributed to a China-linked group, has been identified targeting over 1,000 Small Office/Home Office (SOHO) devices worldwide. This operation, known […]
North Korean Hackers Exploit Fake Zoom Applications to Execute System Takeover Commands
In a sophisticated cyberattack campaign, North Korean-affiliated hackers are targeting professionals by deploying counterfeit Zoom applications designed to execute system takeover commands. This operation combines […]