In the first quarter of 2025, Apple experienced a significant 14% year-over-year increase in iPad shipments, solidifying its dominance in the global tablet market. According […]
Month: May 2025
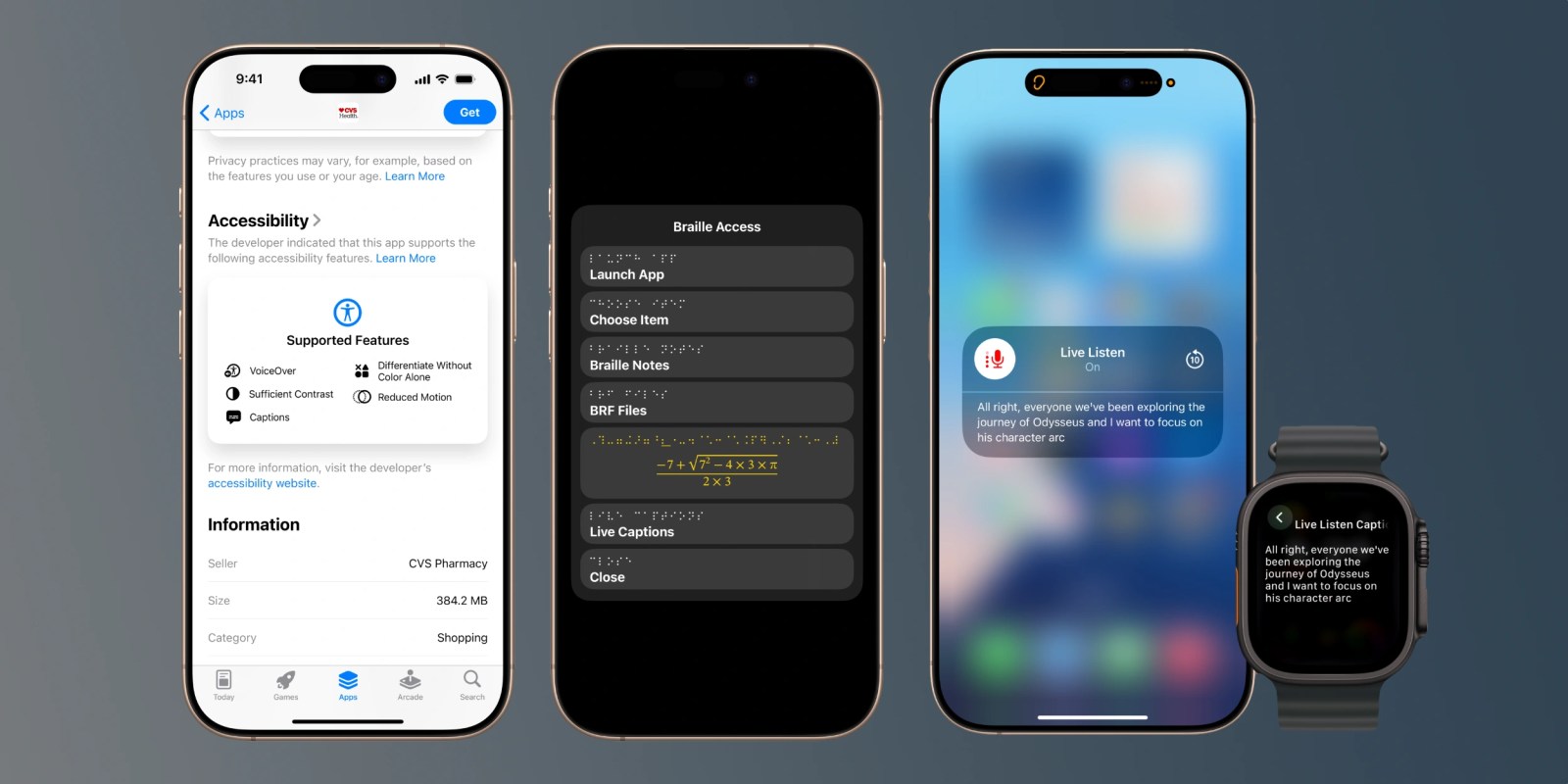
Apple Introduces Enhanced Accessibility Features in iOS 19 and macOS 16
In a significant move to bolster inclusivity, Apple has unveiled a suite of new accessibility features set to debut in the upcoming iOS 19 and […]
[May-13-2025] Daily Cybersecurity Threat Report
I. Introduction This report provides an analysis of cyber threat incidents reported on May 13, 2025, focusing on data breaches, website defacements, and ransomware attacks. […]
PupkinStealer: A New .NET-Based Malware Exploiting Telegram for Data Theft
In April 2025, cybersecurity researchers identified a new information-stealing malware named PupkinStealer. Developed in C# using the .NET framework, this lightweight yet potent malware targets […]
Critical Vulnerability in Linux Kernel’s nftables Subsystem: Exploit Details and Mitigation Strategies
A significant security flaw has been identified in the Linux kernel’s nftables subsystem, designated as CVE-2024-26809. This vulnerability, rooted in the kernel’s netfilter infrastructure, poses […]
Critical Vulnerabilities in Mitel SIP Phones Expose Systems to Remote Command Injection
Recent security analyses have uncovered critical vulnerabilities in Mitel’s SIP phone series, notably the 6800, 6900, and 6900w models, including the 6970 Conference Unit. These […]
Emerging Phishing Tactics Exploit Blob URLs to Evade Detection
Cybersecurity experts have recently identified a sophisticated phishing technique that leverages blob Uniform Resource Identifiers (URIs) to bypass Secure Email Gateways (SEGs) and evade traditional […]
New Technique Enables Attackers to Obtain Microsoft Entra Refresh Tokens via Cobalt Strike Beacon
A recently disclosed method allows attackers to extract Microsoft Entra refresh tokens from compromised endpoints using Cobalt Strike Beacon. This technique poses a significant threat […]
Exploiting Microsoft Copilot AI in SharePoint: A New Frontier for Cyber Threats
The integration of artificial intelligence into enterprise environments has revolutionized productivity and collaboration. Microsoft’s Copilot AI, embedded within SharePoint, exemplifies this transformation by assisting users […]
Hackers Exploit Legacy Protocols in Microsoft Entra ID to Bypass MFA and Conditional Access
Between March 18 and April 7, 2025, cybersecurity researchers identified a sophisticated campaign targeting Microsoft Entra ID by exploiting legacy authentication protocols. This campaign allowed […]

![[May-13-2025] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)






