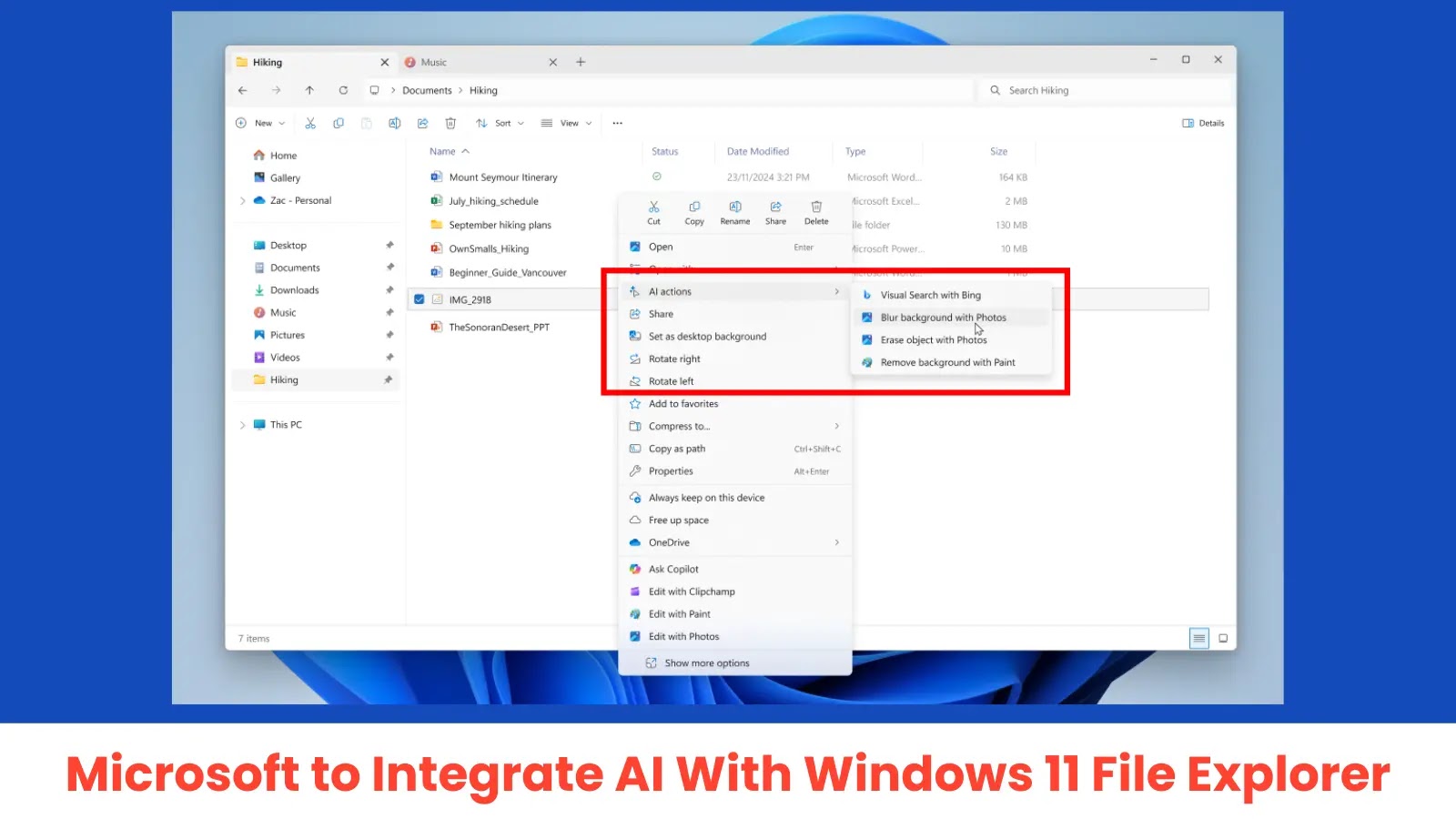
Microsoft is revolutionizing file management in Windows 11 by embedding artificial intelligence (AI) directly into File Explorer. This integration, introduced in Windows 11 Insider Preview […]
Month: May 2025
Critical Vulnerability in Motors WordPress Theme Exposes 22,000 Websites to Potential Takeover
A significant security flaw has been identified in the widely-used Motors WordPress theme, placing approximately 22,000 websites at substantial risk. This critical vulnerability, designated as […]
Critical Vulnerabilities in VMware Cloud Foundation Expose Sensitive Data
Recent security assessments have uncovered multiple high-severity vulnerabilities in VMware Cloud Foundation, a comprehensive hybrid cloud platform utilized for managing enterprise applications across private and […]
Qilin Ransomware Exploits SAP Zero-Day Vulnerability Prior to Public Disclosure
In a recent cybersecurity incident, the Russian-speaking cybercrime group Qilin exploited a critical zero-day vulnerability in SAP NetWeaver Visual Composer, designated as CVE-2025-31324, weeks before […]
Serviceaide Data Breach Exposes Sensitive Information of 480,000 Catholic Health Patients
In a significant cybersecurity incident, Serviceaide, Inc., a provider of IT support management services, has reported a data breach affecting approximately 480,000 patients associated with […]
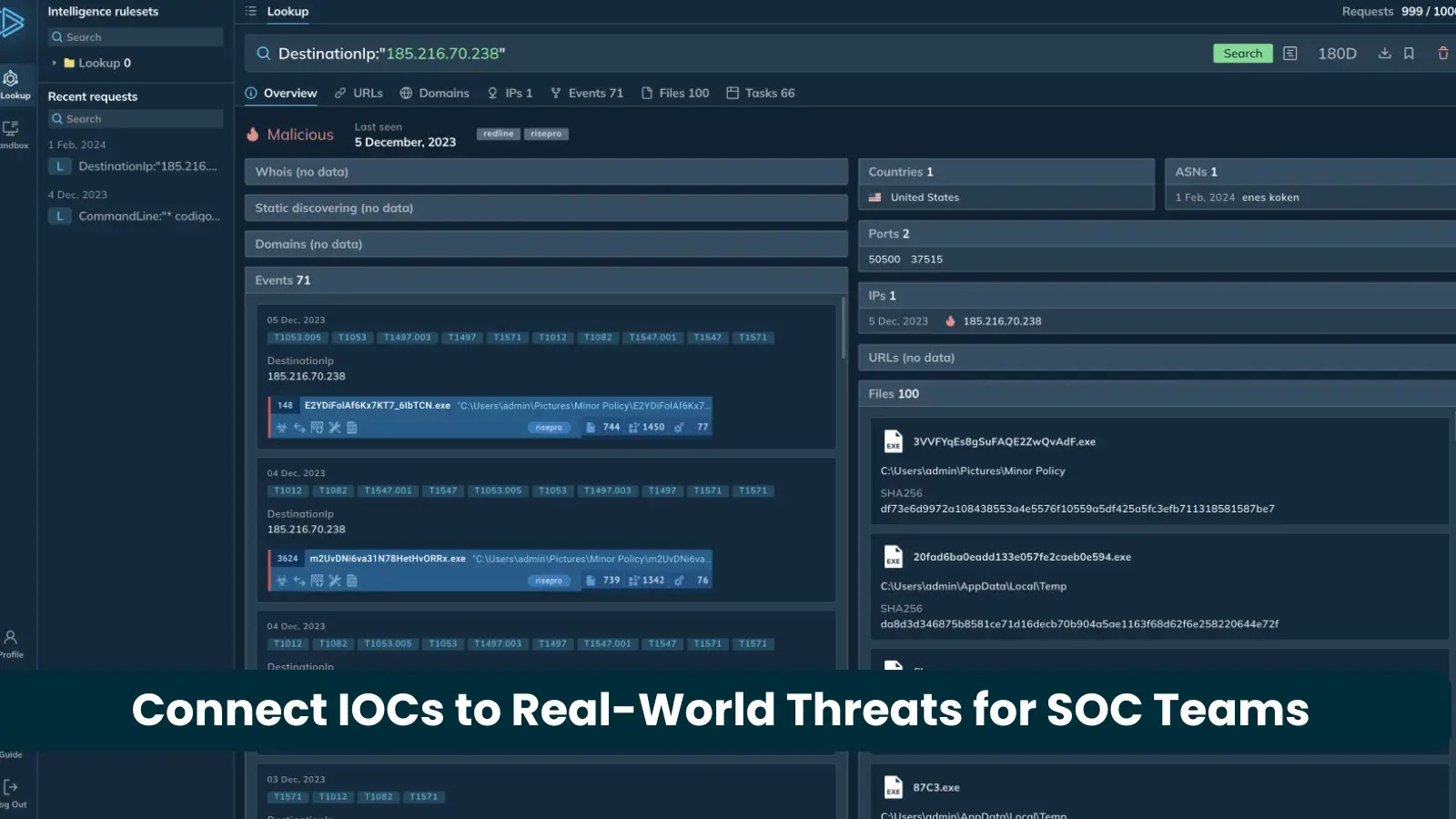
Enhancing SOC Operations: Five Strategies to Link IOCs to Real-World Threats
In the ever-evolving landscape of cybersecurity, Security Operations Center (SOC) teams are inundated with Indicators of Compromise (IOCs). These IOCs—such as suspicious IP addresses, unusual […]
CISA Adds MDaemon Email Server XSS Vulnerability to Known Exploited Vulnerabilities Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has recently expanded its Known Exploited Vulnerabilities (KEV) Catalog to include a significant security flaw affecting the MDaemon […]
Malicious PyPI Packages Exploit Instagram and TikTok APIs to Validate User Accounts
Cybersecurity researchers have recently identified malicious packages uploaded to the Python Package Index (PyPI) repository. These packages function as tools to verify stolen email addresses […]
Go-Based Malware Exploits Redis Servers to Deploy XMRig Miner on Linux Systems
Cybersecurity researchers have identified a new cryptojacking campaign, dubbed RedisRaider, that targets publicly accessible Redis servers to deploy XMRig cryptocurrency miners on Linux systems. This […]
Chinese Cyber Espionage Group UnsolicitedBooker Deploys MarsSnake Backdoor in Prolonged Attack on Saudi Organization
In a series of sophisticated cyber espionage operations, the China-aligned threat actor known as UnsolicitedBooker has been implicated in targeting an undisclosed international organization based […]