The release of Apple’s M4 MacBook Air has sparked interest among users curious about its gaming performance. Equipped with the advanced M4 chip, this laptop […]
Month: May 2025
Transform Your iPhone or iPad into a Versatile Stream Deck with Mobility
In the realm of digital content creation and productivity, the ability to streamline workflows and enhance efficiency is paramount. Traditionally, physical stream decks have been […]
How to Set Dynamic Day and Night Wallpapers on Your iPhone
Personalizing your iPhone’s appearance can enhance your user experience, and one effective way to do this is by setting dynamic wallpapers that change based on […]
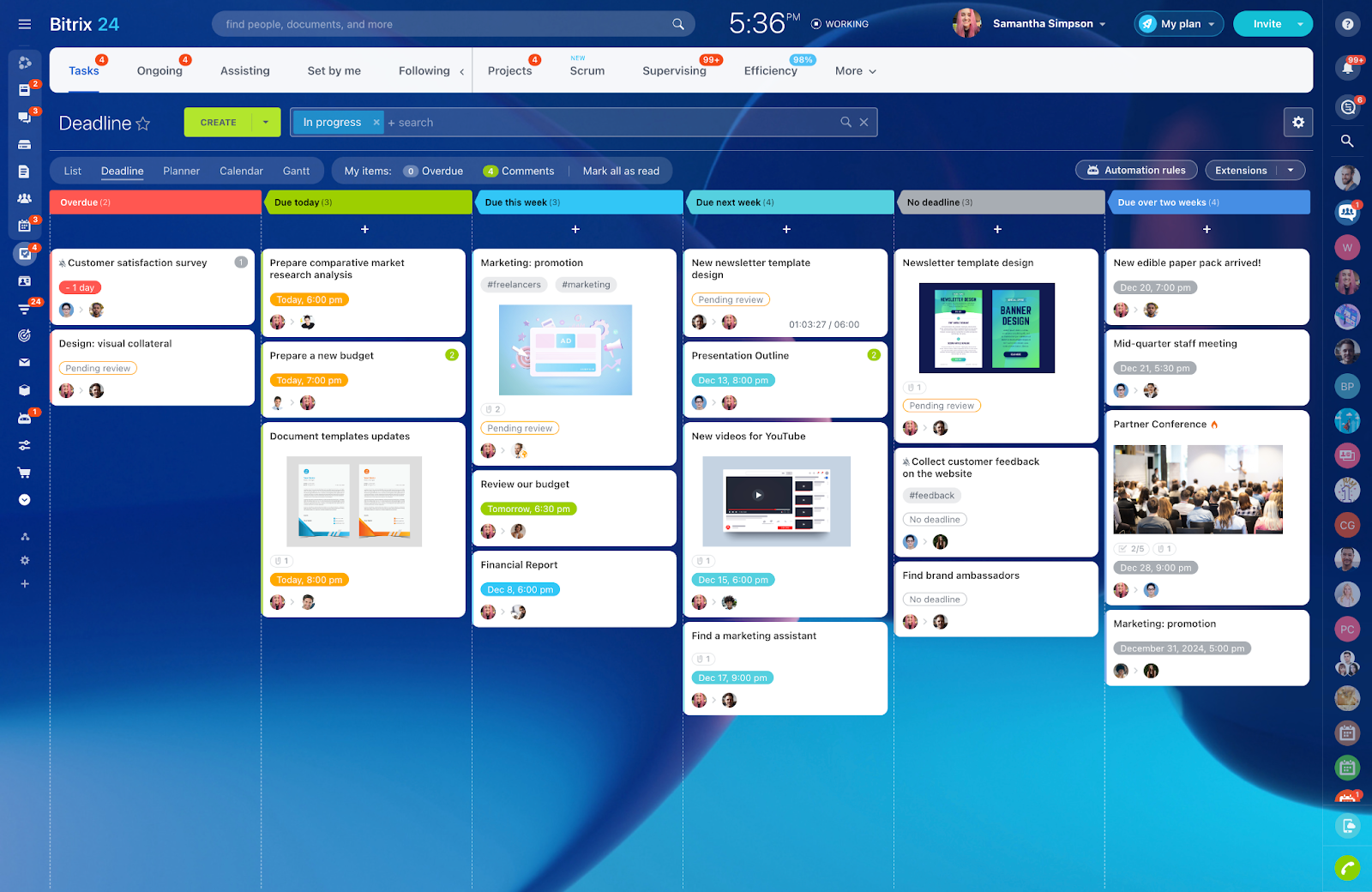
Enhancing Team Collaboration and Project Management with Bitrix24
In today’s fast-paced business environment, effective project and task management are crucial for organizational success. Bitrix24 emerges as a comprehensive solution, offering a suite of […]
Top Apple Deals on Amazon This Memorial Day 2025
Memorial Day 2025 brings a host of enticing deals for Apple enthusiasts on Amazon. Whether you’re in the market for a new iPad, MacBook, Apple […]
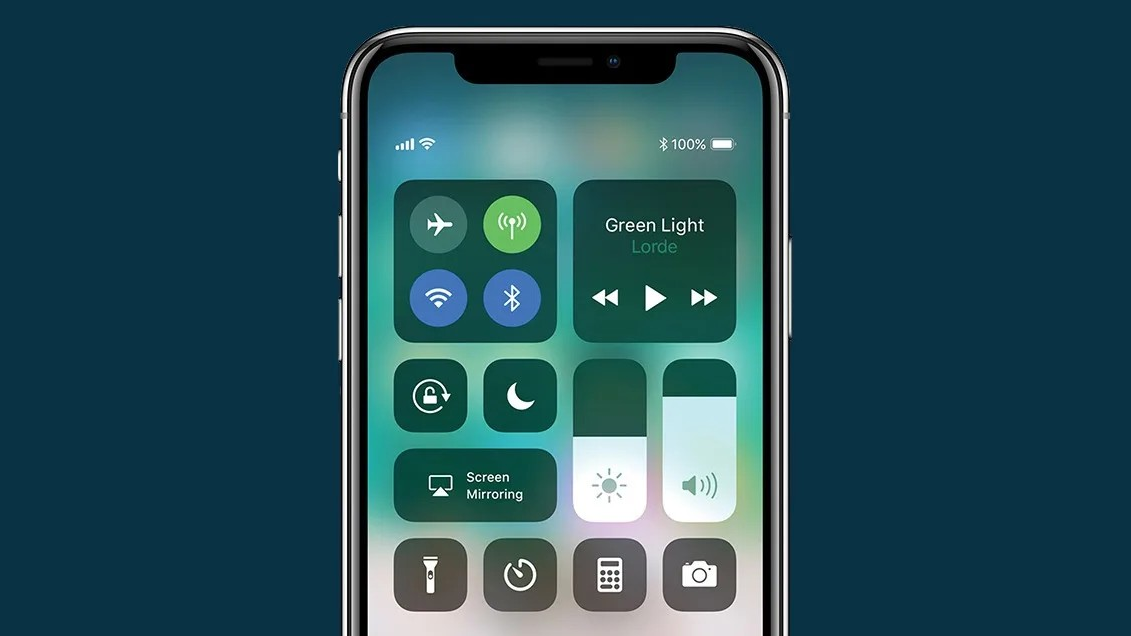
Android’s Quick Panel Mirrors iOS, Yet Apple Maintains Its Edge
The ongoing rivalry between Android and iOS has led to a continuous exchange of design and functionality features. With the introduction of iOS 18, Apple’s […]
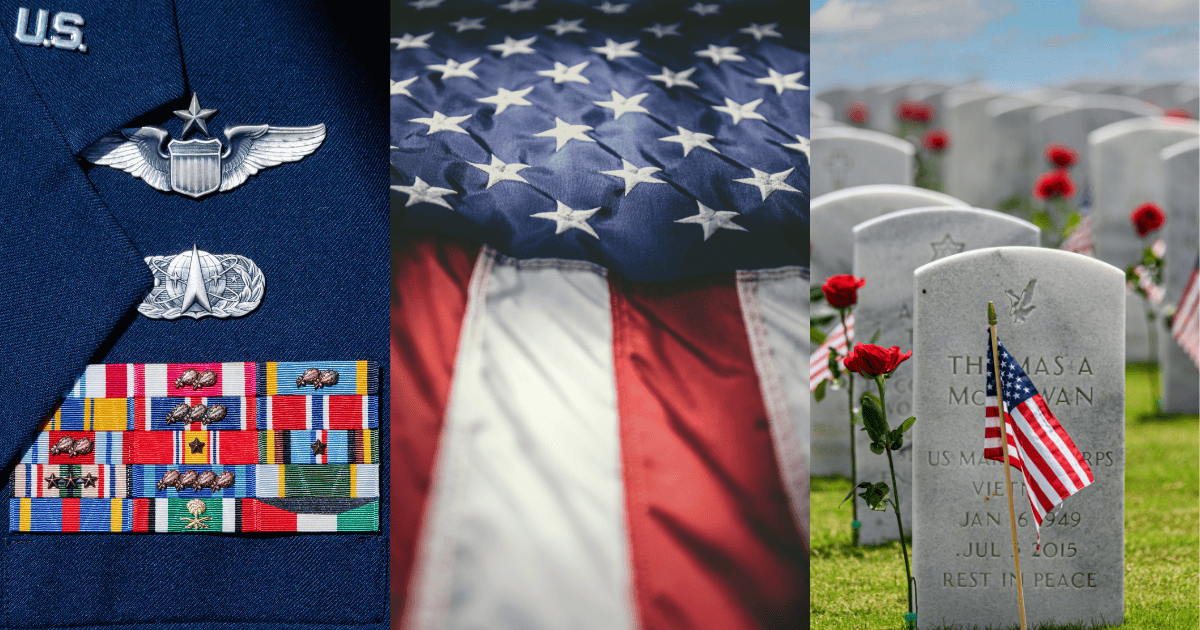
10 Memorial Day Wallpapers for iPhone and Mac (2025)
Memorial Day serves as a solemn occasion to honor and remember the brave men and women who have sacrificed their lives in service to the […]
[May-26-2025] Daily Cybersecurity Threat Report
I. Executive Summary The past 24 hours have underscored a dynamic and increasingly complex cybersecurity landscape, marked by a notable convergence of traditional cybercriminal activities […]
[May-25-2025] Daily Cybersecurity Threat Report
I. Executive Summary The past 24 hours have revealed a diverse and active cybersecurity landscape, primarily characterized by widespread data breaches, targeted initial access attempts, […]
[May-24-2025] Daily Cybersecurity Threat Report
I. Executive Summary The reporting period reveals a persistently active and complex cybersecurity landscape, marked by a significant interplay between hacktivist operations, geopolitical tensions, and […]




![[May-26-2025] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)