In a sophisticated cyberattack campaign known as ClickFix, threat actors are leveraging counterfeit Google Meet pages to deceive users into executing malicious PowerShell commands, resulting […]
Month: May 2025
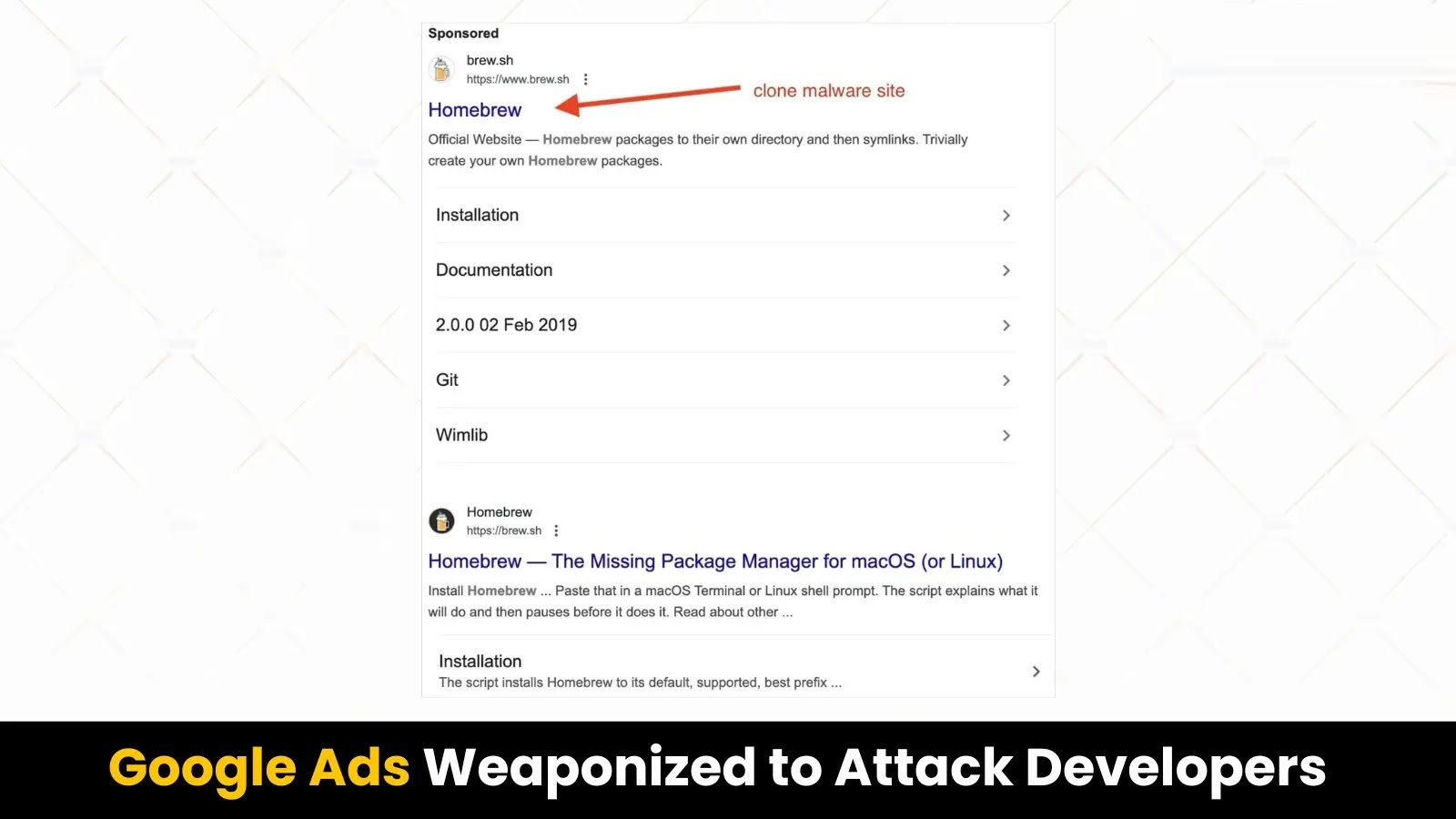
Cybercriminals Exploit Google Ads to Distribute AmosStealer via Fake Homebrew Site
In a recent and sophisticated cyberattack, malicious actors have been leveraging Google Ads to deceive macOS and Linux users into downloading the AmosStealer malware through […]
Exploiting HTTP/2 Vulnerabilities: New Cross-Origin Attack Vectors Unveiled
Recent research has uncovered critical vulnerabilities within the HTTP/2 protocol, enabling attackers to bypass established web security measures and execute arbitrary cross-site scripting (XSS) attacks […]
Red Hat and AMD Collaborate to Enhance AI Processing Power and Performance
In a significant move to bolster artificial intelligence (AI) capabilities, Red Hat and AMD have announced a strategic partnership aimed at enhancing processing power and […]
Critical Vulnerabilities in GIMP Image Editor Allow Remote Code Execution
Two significant security vulnerabilities have been identified in the GNU Image Manipulation Program (GIMP), a widely used open-source image editing software. These vulnerabilities, designated as […]
Adidas Data Breach Exposes Customer Information Through Third-Party Service Provider
On May 23, 2025, Adidas, the renowned German sportswear company, disclosed a significant data breach involving customer information accessed via a compromised third-party customer service […]
Critical Vulnerability in GitHub MCP Server Exposes Private Repositories
A significant security flaw has been identified in GitHub’s Model Context Protocol (MCP) server, potentially allowing unauthorized access to private repositories through sophisticated prompt injection […]
Windows 11 Notepad Introduces AI-Powered ‘Write’ Feature for Enhanced Text Generation
Microsoft has significantly upgraded its longstanding Notepad application by integrating an AI-driven text generation feature named Write. This enhancement marks a substantial evolution for the […]
Critical Vulnerability in Arm Mali GPU Driver Enables MTE Bypass and Arbitrary Kernel Code Execution
Security researchers have identified a critical vulnerability in Arm’s Mali GPU driver, designated as CVE-2025-0072, which allows malicious Android applications to bypass Memory Tagging Extension […]
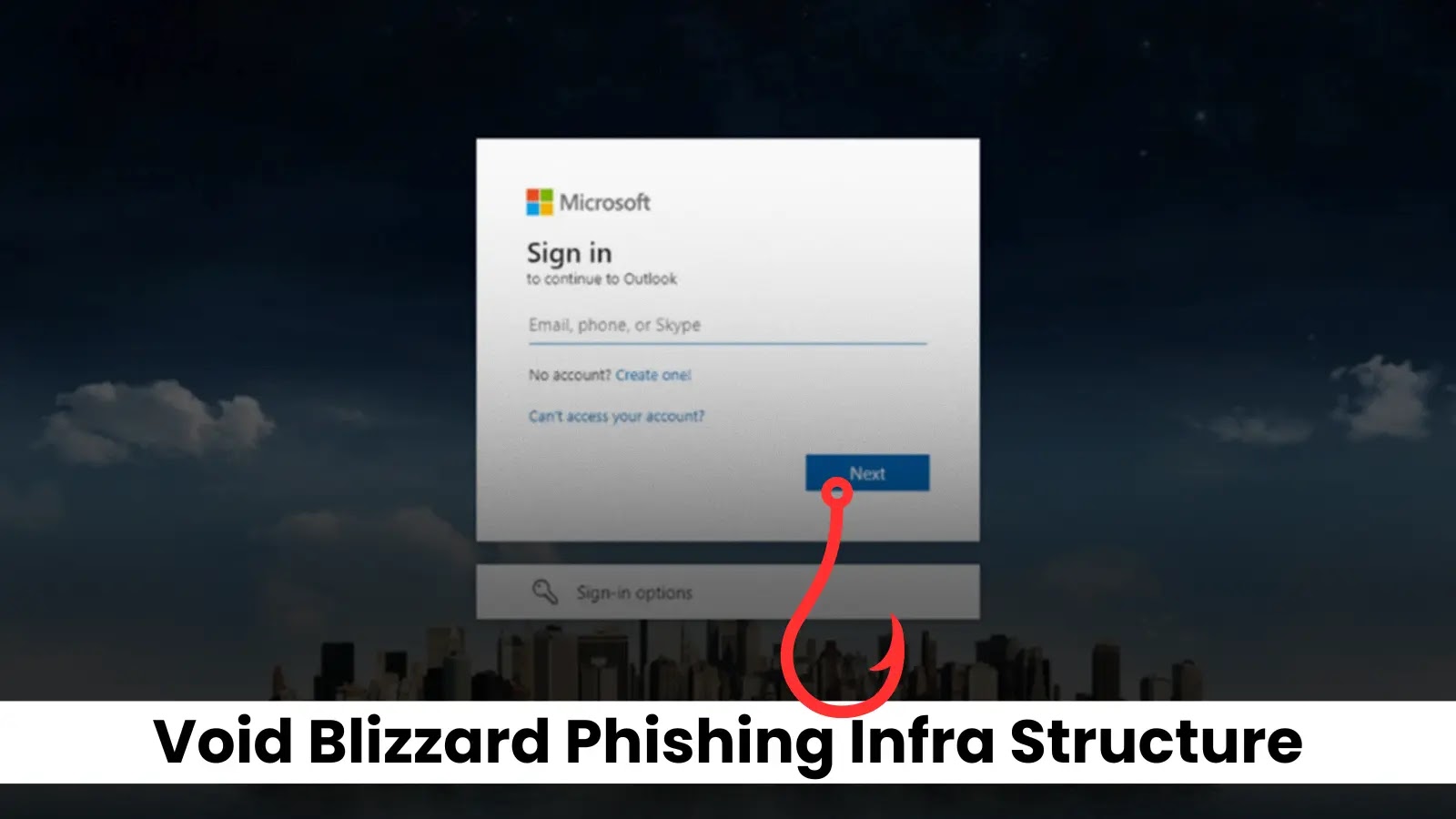
Russian Cyber Espionage Group ‘Void Blizzard’ Targets Critical Infrastructure Across Europe and North America
Microsoft Threat Intelligence has identified a sophisticated Russian-affiliated cyber espionage group, dubbed Void Blizzard (also known as LAUNDRY BEAR), actively targeting telecommunications and IT organizations […]