In a significant escalation of cyber warfare, Pakistan-affiliated Advanced Persistent Threat (APT) groups, notably APT36 (also known as Transparent Tribe) and its sub-group SideCopy, have […]
Month: May 2025
Securing Supply Chains: Strategies for Mitigating Third-Party Risks
In today’s interconnected global economy, businesses increasingly rely on third-party vendors to enhance operational efficiency and drive innovation. However, this dependency introduces significant risks, as […]
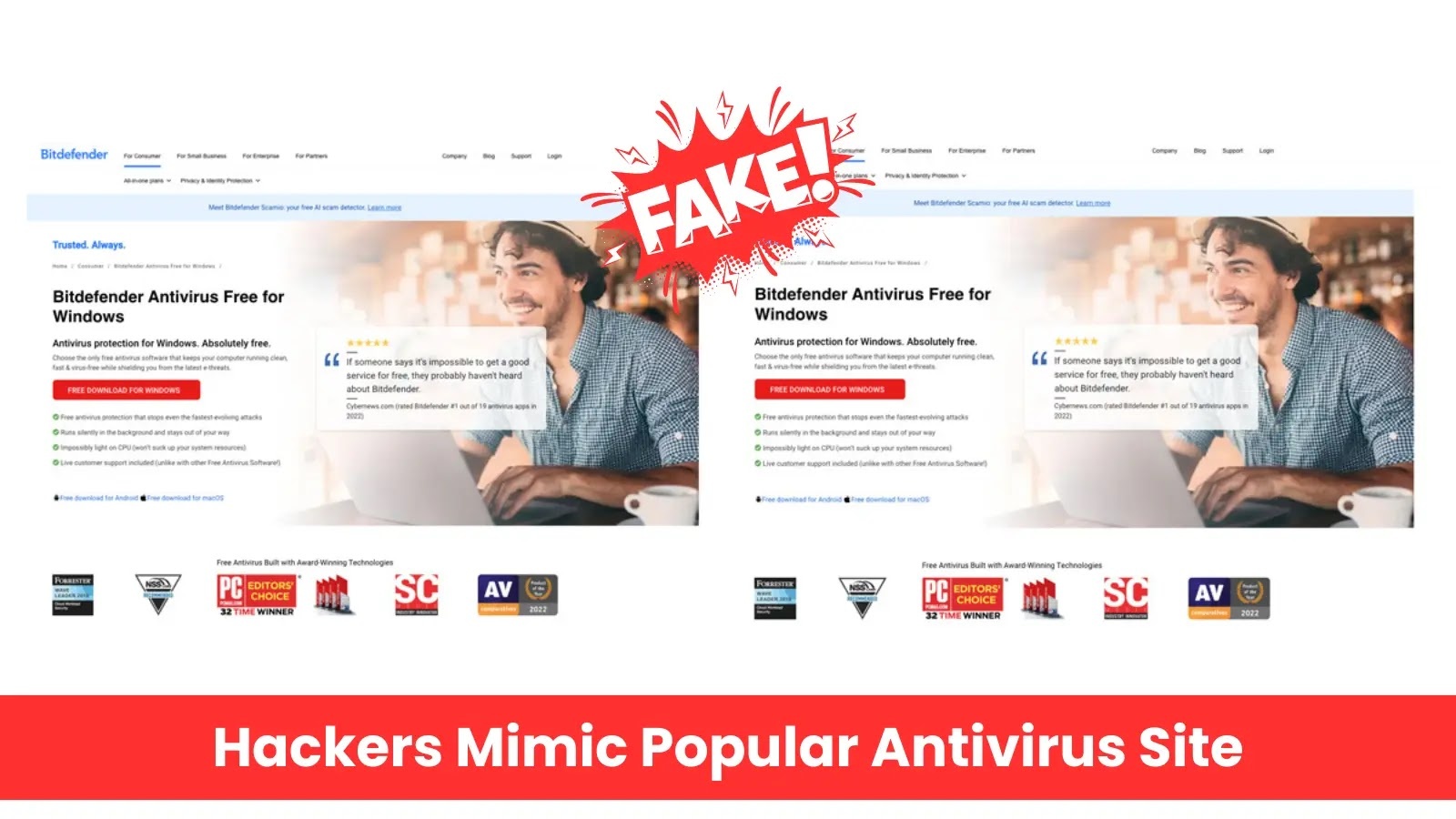
Hackers Impersonate Popular Antivirus Site to Deploy VenomRAT and Steal Financial Data
Cybercriminals have orchestrated a sophisticated malware campaign by creating a counterfeit Bitdefender antivirus website to distribute a trio of malicious programs aimed at stealing financial […]
AT&T Faces Alleged Data Breach: 31 Million Customer Records Exposed
In late May 2025, reports emerged of a significant data breach involving AT&T, one of the United States’ largest telecommunications providers. A threat actor claimed […]
Apple’s Ongoing Battle Against App Store Fraud: A $9 Billion Milestone
In a recent disclosure, Apple announced that it has successfully thwarted over $9 billion in fraudulent transactions on the App Store over the past five […]
Coordinated Cloud-Based Scanning Targets Multiple Vulnerabilities Using Amazon-Hosted IPs
On May 8, 2025, cybersecurity researchers identified a coordinated scanning operation targeting 75 distinct exposure points across various technologies. This activity involved 251 IP addresses, […]
Understanding Browser-in-the-Middle Attacks: A New Threat to Online Security
In the ever-evolving landscape of cybersecurity threats, a new and sophisticated attack vector has emerged: the Browser-in-the-Middle (BitM) attack. This method allows cybercriminals to intercept […]
Mimo Hackers Exploit CVE-2025-32432 in Craft CMS to Deploy Cryptominer and Proxyware
A financially motivated cybercriminal group, identified as Mimo, has been exploiting a critical vulnerability in the Craft Content Management System (CMS) to infiltrate servers and […]
The Rapid Evolution of Stealer Malware: A 24-Hour Enterprise Threat
In the ever-evolving landscape of cyber threats, stealer malware has undergone a significant transformation. No longer confined to pilfering passwords, modern stealers now exfiltrate live […]
Emergence of PumaBot: A New Botnet Targeting Linux IoT Devices for SSH Credential Theft and Cryptomining
A newly identified botnet, dubbed PumaBot, is actively targeting Linux-based Internet of Things (IoT) devices. This malware, written in the Go programming language, employs sophisticated […]