On May 14, 2025, Coinbase Global, Inc., a leading cryptocurrency exchange, disclosed a significant cybersecurity incident in a Form 8-K filing with the U.S. Securities […]
Day: May 16, 2025
Hackers Exploit Google Services to Dispatch Fraudulent Law Enforcement Requests
In a recent and sophisticated phishing campaign, cybercriminals have been exploiting Google’s legitimate services to send fraudulent law enforcement data requests, effectively bypassing traditional security […]
Advanced .NET Multi-Stage Loader Targets Windows Systems with Evasive Malware
Since early 2022, a sophisticated .NET-based multi-stage malware loader has been actively targeting Windows systems, serving as a conduit for deploying various malicious payloads, including […]
CISA Alerts on Actively Exploited Google Chromium Vulnerability – Immediate Action Required
The Cybersecurity and Infrastructure Security Agency (CISA) has recently added a critical vulnerability, identified as CVE-2025-4664, to its Known Exploited Vulnerabilities Catalog. This high-severity flaw […]
Proofpoint to Acquire Hornetsecurity for $1 Billion, Enhancing Microsoft 365 Security Solutions
Proofpoint, Inc., a global leader in cybersecurity and compliance, has announced a definitive agreement to acquire Hornetsecurity Group, a prominent European provider of AI-powered Microsoft […]
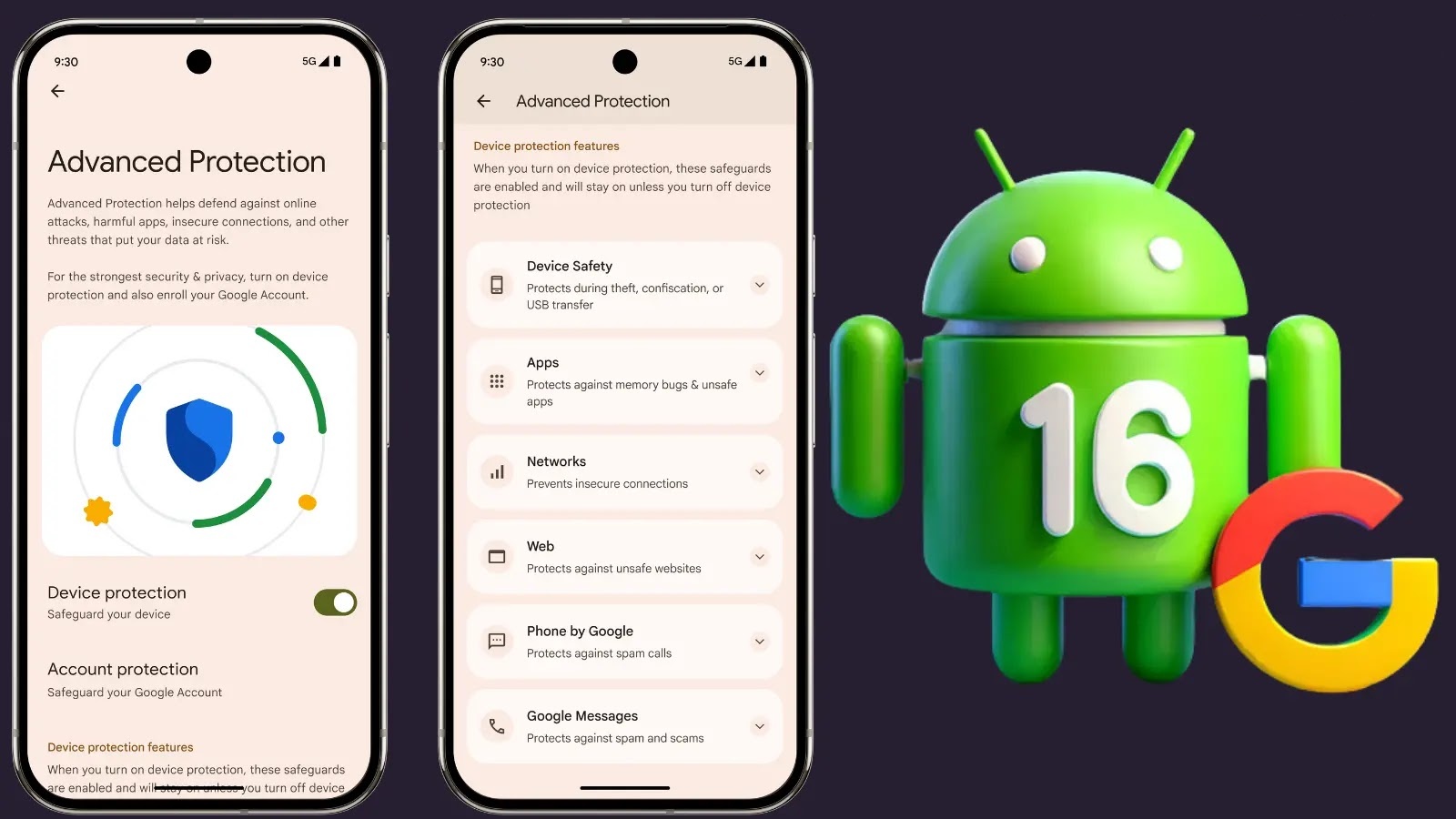
Google Unveils Android 16 with Enhanced Device-Level Security for Over 3 Billion Users
Google has announced a significant enhancement to its Advanced Protection Program with the release of Android 16, introducing robust device-level security settings aimed at safeguarding […]
Critical Vulnerability in SonicWall SMA1000 Series Allows Remote Exploitation via Encoded URLs
SonicWall has recently disclosed a significant security vulnerability in its Secure Mobile Access (SMA) 1000 series appliances, specifically within the WorkPlace interface. This flaw, identified […]
VanHelsing Ransomware: A Comprehensive Analysis of Its Advanced Tactics and Cross-Platform Threat
In March 2025, the cybersecurity community identified a new and sophisticated ransomware-as-a-service (RaaS) operation named VanHelsing. This emerging threat has rapidly gained notoriety due to […]
Commit Stomping: Manipulating Git Timestamps to Conceal Malicious Code Changes
In the realm of software development, Git serves as a cornerstone for version control, enabling teams to track and manage code changes efficiently. However, a […]
Jenkins Security Update Addresses Critical Vulnerabilities in CI/CD Pipelines
The Jenkins project has recently released a critical security advisory detailing multiple vulnerabilities across several widely used plugins, including Cadence vManager, DingTalk, Health Advisor by […]