In today’s digital landscape, cybersecurity has transitioned from a purely technical concern to a critical business imperative. With increasing regulatory demands, sophisticated cyber threats, and […]
Month: April 2025
Outlaw Cybergang Resurfaces with Enhanced Malware Targeting Linux Systems Globally
The cybercriminal group known as Outlaw, active since at least 2018, has re-emerged with a more sophisticated malware toolkit aimed at Linux servers worldwide. Recent […]
Konni APT Group Deploys Multi-Stage Malware in Targeted Attacks on Organizations
The Konni Advanced Persistent Threat (APT) group, a cyber espionage entity with ties to North Korea, has recently intensified its operations by deploying sophisticated multi-stage […]
OpenAI Reverses GPT-4o Update Amid Concerns Over Excessive Agreeableness
OpenAI has recently rolled back its latest update to the GPT-4o model following user reports that the AI exhibited overly agreeable and flattering behavior, a […]
Critical Vulnerability in SonicWall Connect Tunnel Windows Client Enables Denial-of-Service Attacks
A significant security flaw has been identified in the SonicWall Connect Tunnel Windows Client, affecting both 32-bit and 64-bit versions up to 12.4.3.283. This vulnerability, […]
Ascension Healthcare Data Breach Exposes Sensitive Patient Information Through Third-Party Vendor
Ascension Healthcare, one of the largest private healthcare systems in the United States, recently disclosed a significant data breach that compromised sensitive patient information through […]
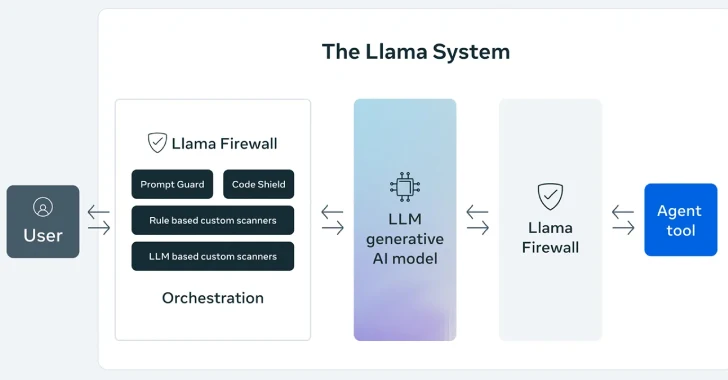
Meta Introduces LlamaFirewall Framework to Enhance AI Security
On April 30, 2025, Meta unveiled LlamaFirewall, an open-source framework designed to bolster the security of artificial intelligence (AI) systems against emerging cyber threats such […]
Indian Court Orders Blocking of Proton Mail Amid AI Deepfake Abuse Allegations
In a significant legal development, the High Court of Karnataka has mandated the nationwide blocking of Proton Mail, an end-to-end encrypted email service, following allegations […]
Customer Account Takeovers: The Multi-Billion Dollar Problem You Don’t Know About
In today’s digital age, the security of online accounts is paramount. Yet, many users have encountered unsettling scenarios: logging into a streaming service only to […]
RansomHub’s Sudden Disappearance Sparks Turmoil Among Affiliates
In a surprising turn of events, the notorious ransomware-as-a-service (RaaS) operation known as RansomHub has mysteriously ceased its online activities as of April 1, 2025. […]